Cisco
GRE over IPsecのデバッグログ
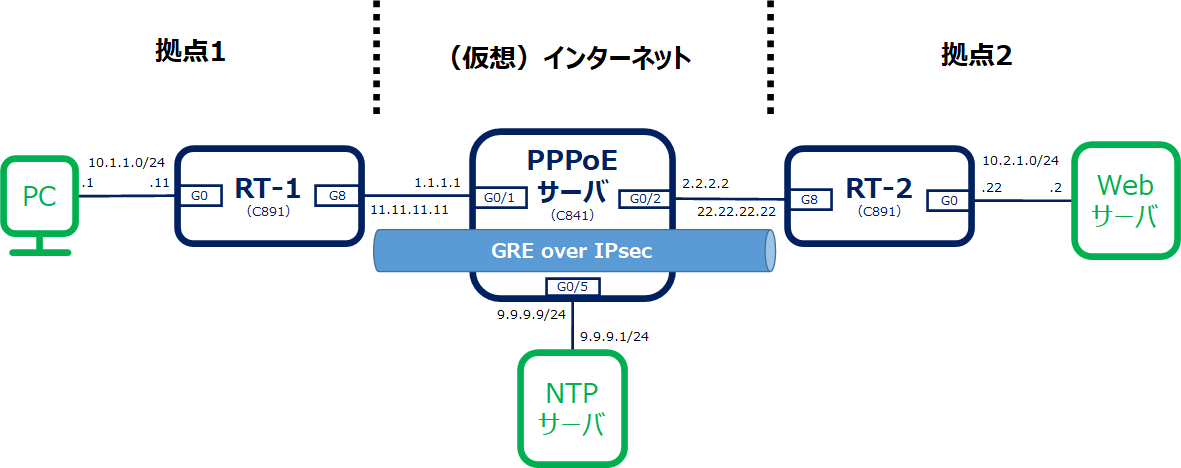
構成図
GRE over IPsecのコンフィグで、IPsecが接続される際のデバッグログを記録します。
RT-1のデバッグログ(レスポンダーとして動作)
RT-1#
025898: Mar 17 01:05:16.794: ISAKMP (0): received packet from 22.22.22.22 dport 500 sport 500 Global (N) NEW SA
025899: Mar 17 01:05:16.794: ISAKMP: Created a peer struct for 22.22.22.22, peer port 500
025900: Mar 17 01:05:16.794: ISAKMP: New peer created peer = 0x12021B28 peer_handle = 0x8000000E
025901: Mar 17 01:05:16.794: ISAKMP: Locking peer struct 0x12021B28, refcount 1 for crypto_isakmp_process_block
025902: Mar 17 01:05:16.794: ISAKMP: local port 500, remote port 500
025903: Mar 17 01:05:16.794: ISAKMP: Find a dup sa in the avl tree during calling isadb_insert sa = 2C62D70
025904: Mar 17 01:05:16.794: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
025905: Mar 17 01:05:16.794: ISAKMP:(0):Old State = IKE_READY New State = IKE_R_MM1
025906: Mar 17 01:05:16.794: ISAKMP:(0): processing SA payload. message ID = 0
025907: Mar 17 01:05:16.794: ISAKMP:(0): processing vendor id payload
025908: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
025909: Mar 17 01:05:16.794: ISAKMP (0): vendor ID is NAT-T RFC 3947
025910: Mar 17 01:05:16.794: ISAKMP:(0): processing vendor id payload
025911: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID seems Unity/DPD but major 245 mismatch
025912: Mar 17 01:05:16.794: ISAKMP (0): vendor ID is NAT-T v7
025913: Mar 17 01:05:16.794: ISAKMP:(0): processing vendor id payload
025914: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID seems Unity/DPD but major 157 mismatch
025915: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID is NAT-T v3
025916: Mar 17 01:05:16.794: ISAKMP:(0): processing vendor id payload
025917: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
025918: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID is NAT-T v2
025919: Mar 17 01:05:16.794: ISAKMP:(0):found peer pre-shared key matching 22.22.22.22
025920: Mar 17 01:05:16.794: ISAKMP:(0): local preshared key found
025921: Mar 17 01:05:16.794: ISAKMP : Scanning profiles for xauth ...
025922: Mar 17 01:05:16.794: ISAKMP:(0):Checking ISAKMP transform 1 against priority 110 policy
025923: Mar 17 01:05:16.794: ISAKMP: encryption AES-CBC
025924: Mar 17 01:05:16.794: ISAKMP: keylength of 128
025925: Mar 17 01:05:16.794: ISAKMP: hash SHA256
025926: Mar 17 01:05:16.794: ISAKMP: default group 2
025927: Mar 17 01:05:16.794: ISAKMP: auth pre-share
025928: Mar 17 01:05:16.794: ISAKMP: life type in seconds
025929: Mar 17 01:05:16.794: ISAKMP: life duration (basic) of 1800
025930: Mar 17 01:05:16.794: ISAKMP:(0):atts are acceptable. Next payload is 0
025931: Mar 17 01:05:16.794: ISAKMP:(0):Acceptable atts:actual life: 1800
025932: Mar 17 01:05:16.794: ISAKMP:(0):Acceptable atts:life: 0
025933: Mar 17 01:05:16.794: ISAKMP:(0):Basic life_in_seconds:1800
025934: Mar 17 01:05:16.794: ISAKMP:(0):Returning Actual lifetime: 1800
025935: Mar 17 01:05:16.794: ISAKMP:(0)::Started lifetime timer: 1800.
025936: Mar 17 01:05:16.794: ISAKMP:(0): processing vendor id payload
025937: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
025938: Mar 17 01:05:16.794: ISAKMP (0): vendor ID is NAT-T RFC 3947
025939: Mar 17 01:05:16.794: ISAKMP:(0): processing vendor id payload
025940: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID seems Unity/DPD but major 245 mismatch
025941: Mar 17 01:05:16.794: ISAKMP (0): vendor ID is NAT-T v7
025942: Mar 17 01:05:16.794: ISAKMP:(0): processing vendor id payload
025943: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID seems Unity/DPD but major 157 mismatch
025944: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID is NAT-T v3
025945: Mar 17 01:05:16.794: ISAKMP:(0): processing vendor id payload
025946: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
025947: Mar 17 01:05:16.794: ISAKMP:(0): vendor ID is NAT-T v2
025948: Mar 17 01:05:16.794: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
025949: Mar 17 01:05:16.794: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM1
025950: Mar 17 01:05:16.794: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID
025951: Mar 17 01:05:16.794: ISAKMP:(0): sending packet to 22.22.22.22 my_port 500 peer_port 500 (R) MM_SA_SETUP
025952: Mar 17 01:05:16.794: ISAKMP:(0):Sending an IKE IPv4 Packet.
025953: Mar 17 01:05:16.794: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
025954: Mar 17 01:05:16.794: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM2
025955: Mar 17 01:05:16.798: ISAKMP (0): received packet from 22.22.22.22 dport 500 sport 500 Global (R) MM_SA_SETUP
025956: Mar 17 01:05:16.798: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
025957: Mar 17 01:05:16.798: ISAKMP:(0):Old State = IKE_R_MM2 New State = IKE_R_MM3
025958: Mar 17 01:05:16.798: ISAKMP:(0): processing KE payload. message ID = 0
025959: Mar 17 01:05:16.802: ISAKMP:(0): processing NONCE payload. message ID = 0
025960: Mar 17 01:05:16.802: ISAKMP:(0):found peer pre-shared key matching 22.22.22.22
025961: Mar 17 01:05:16.802: ISAKMP:(2024): processing vendor id payload
025962: Mar 17 01:05:16.802: ISAKMP:(2024): vendor ID is DPD
025963: Mar 17 01:05:16.802: ISAKMP:(2024): processing vendor id payload
025964: Mar 17 01:05:16.802: ISAKMP:(2024): speaking to another IOS box!
025965: Mar 17 01:05:16.802: ISAKMP:(2024): processing vendor id payload
025966: Mar 17 01:05:16.802: ISAKMP:(2024): vendor ID seems Unity/DPD but major 80 mismatch
025967: Mar 17 01:05:16.802: ISAKMP:(2024): vendor ID is XAUTH
025968: Mar 17 01:05:16.802: ISAKMP:received payload type 20
025969: Mar 17 01:05:16.802: ISAKMP (2024): His hash no match - this node outside NAT
025970: Mar 17 01:05:16.802: ISAKMP:received payload type 20
025971: Mar 17 01:05:16.802: ISAKMP (2024): No NAT Found for self or peer
025972: Mar 17 01:05:16.802: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
025973: Mar 17 01:05:16.802: ISAKMP:(2024):Old State = IKE_R_MM3 New State = IKE_R_MM3
025974: Mar 17 01:05:16.802: ISAKMP:(2024): sending packet to 22.22.22.22 my_port 500 peer_port 500 (R) MM_KEY_EXCH
025975: Mar 17 01:05:16.802: ISAKMP:(2024):Sending an IKE IPv4 Packet.
025976: Mar 17 01:05:16.802: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
025977: Mar 17 01:05:16.802: ISAKMP:(2024):Old State = IKE_R_MM3 New State = IKE_R_MM4
025978: Mar 17 01:05:16.810: ISAKMP (2024): received packet from 22.22.22.22 dport 500 sport 500 Global (R) MM_KEY_EXCH
025979: Mar 17 01:05:16.810: ISAKMP:(2024):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
025980: Mar 17 01:05:16.810: ISAKMP:(2024):Old State = IKE_R_MM4 New State = IKE_R_MM5
025981: Mar 17 01:05:16.810: ISAKMP:(2024): processing ID payload. message ID = 0
025982: Mar 17 01:05:16.810: ISAKMP (2024): ID payload
next-payload : 8
type : 1
address : 22.22.22.22
protocol : 17
port : 500
length : 12
025983: Mar 17 01:05:16.810: ISAKMP:(0):: peer matches *none* of the profiles
025984: Mar 17 01:05:16.810: ISAKMP:(2024): processing HASH payload. message ID = 0
025985: Mar 17 01:05:16.810: ISAKMP:received payload type 17
025986: Mar 17 01:05:16.810: ISAKMP:(2024): processing NOTIFY INITIAL_CONTACT protocol 1
spi 0, message ID = 0, sa = 0x2C62D70
025987: Mar 17 01:05:16.810: ISAKMP:(2024):SA authentication status:
authenticated
025988: Mar 17 01:05:16.810: ISAKMP:(2024):SA has been authenticated with 22.22.22.22
025989: Mar 17 01:05:16.810: ISAKMP:(2024):SA authentication status:
authenticated
025990: Mar 17 01:05:16.810: ISAKMP:(2024): Process initial contact,
bring down existing phase 1 and 2 SA's with local 11.11.11.11 remote 22.22.22.22 remote port 500
025991: Mar 17 01:05:16.810: ISAKMP: Trying to insert a peer 11.11.11.11/22.22.22.22/500/, and inserted successfully 12021B28.
025992: Mar 17 01:05:16.810: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
025993: Mar 17 01:05:16.810: ISAKMP:(2024):Old State = IKE_R_MM5 New State = IKE_R_MM5
025994: Mar 17 01:05:16.810: IPSEC(key_engine): got a queue event with 1 KMI message(s)
025995: Mar 17 01:05:16.810: ISAKMP:(2024):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
025996: Mar 17 01:05:16.810: ISAKMP (2024): ID payload
next-payload : 8
type : 1
address : 11.11.11.11
protocol : 17
port : 500
length : 12
025997: Mar 17 01:05:16.810: ISAKMP:(2024):Total payload length: 12
025998: Mar 17 01:05:16.810: ISAKMP:(2024): sending packet to 22.22.22.22 my_port 500 peer_port 500 (R) MM_KEY_EXCH
025999: Mar 17 01:05:16.810: ISAKMP:(2024):Sending an IKE IPv4 Packet.
026000: Mar 17 01:05:16.810: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
026001: Mar 17 01:05:16.810: ISAKMP:(2024):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
026002: Mar 17 01:05:16.810: ISAKMP:(2024):IKE_DPD is enabled, initializing timers
026003: Mar 17 01:05:16.810: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
026004: Mar 17 01:05:16.810: ISAKMP:(2024):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
026005: Mar 17 01:05:16.814: ISAKMP (2024): received packet from 22.22.22.22 dport 500 sport 500 Global (R) QM_IDLE
026006: Mar 17 01:05:16.814: ISAKMP: set new node 1882507048 to QM_IDLE
026007: Mar 17 01:05:16.814: ISAKMP:(2024): processing HASH payload. message ID = 1882507048
026008: Mar 17 01:05:16.814: ISAKMP:(2024): processing SA payload. message ID = 1882507048
026009: Mar 17 01:05:16.814: ISAKMP:(2024):Checking IPSec proposal 1
026010: Mar 17 01:05:16.814: ISAKMP: transform 1, ESP_AES
026011: Mar 17 01:05:16.814: ISAKMP: attributes in transform:
026012: Mar 17 01:05:16.814: ISAKMP: encaps is 2 (Transport)
026013: Mar 17 01:05:16.814: ISAKMP: SA life type in seconds
026014: Mar 17 01:05:16.814: ISAKMP: SA life duration (basic) of 1200
026015: Mar 17 01:05:16.814: ISAKMP: SA life type in kilobytes
026016: Mar 17 01:05:16.814: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
026017: Mar 17 01:05:16.814: ISAKMP: authenticator is HMAC-SHA256
026018: Mar 17 01:05:16.814: ISAKMP: key length is 128
026019: Mar 17 01:05:16.814: ISAKMP: group is 14
026020: Mar 17 01:05:16.814: ISAKMP:(2024):atts are acceptable.
026021: Mar 17 01:05:16.814: IPSEC(validate_proposal_request): proposal part #1
026022: Mar 17 01:05:16.814: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 11.11.11.11/255.255.255.255/47/0,
remote_proxy= 22.22.22.22/255.255.255.255/47/0,
protocol= ESP, transform= NONE (Transport),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
026023: Mar 17 01:05:16.814: Cannot find crypto swsb for idb Tunnel0: in ipsec_process_proposal (), 1206
026024: Mar 17 01:05:16.814: IPSEC(ipsec_process_proposal): TP not configured or sadb not init for idb Tunnel0
026025: Mar 17 01:05:16.814: Crypto mapdb : proxy_match
src addr : 11.11.11.11
dst addr : 22.22.22.22
protocol : 47
src port : 0
dst port : 0
026026: Mar 17 01:05:16.814: (ipsec_process_proposal)Map Accepted: MAP-name, 160
026027: Mar 17 01:05:16.814: ISAKMP:(2024): processing NONCE payload. message ID = 1882507048
026028: Mar 17 01:05:16.818: ISAKMP:(2024): processing KE payload. message ID = 1882507048
026029: Mar 17 01:05:16.830: ISAKMP:(2024): processing ID payload. message ID = 1882507048
026030: Mar 17 01:05:16.830: ISAKMP:(2024): processing ID payload. message ID = 1882507048
026031: Mar 17 01:05:16.830: ISAKMP:(2024):QM Responder gets spi
026032: Mar 17 01:05:16.830: ISAKMP:(2024):Node 1882507048, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
026033: Mar 17 01:05:16.830: ISAKMP:(2024):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
026034: Mar 17 01:05:16.830: ISAKMP:(2024):Node 1882507048, Input = IKE_MESG_INTERNAL, IKE_GOT_SPI
026035: Mar 17 01:05:16.830: ISAKMP:(2024):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_IPSEC_INSTALL_AWAIT
026036: Mar 17 01:05:16.830: IPSEC(key_engine): got a queue event with 1 KMI message(s)
026037: Mar 17 01:05:16.830: Crypto mapdb : proxy_match
src addr : 11.11.11.11
dst addr : 22.22.22.22
protocol : 47
src port : 0
dst port : 0
026038: Mar 17 01:05:16.830: IPSEC(crypto_ipsec_create_ipsec_sas): Map found MAP-name, 160
026039: Mar 17 01:05:16.830: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and peer 22.22.22.22
026040: Mar 17 01:05:16.830: IPSEC(create_sa): sa created,
(sa) sa_dest= 11.11.11.11, sa_proto= 50,
sa_spi= 0x7B2235E(129114974),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 57
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 11.11.11.11/255.255.255.255/47/0,
remote_proxy= 22.22.22.22/255.255.255.255/47/0
026041: Mar 17 01:05:16.830: IPSEC(create_sa): sa created,
(sa) sa_dest= 22.22.22.22, sa_proto= 50,
sa_spi= 0x259C42D3(630997715),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 58
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 11.11.11.11/255.255.255.255/47/0,
remote_proxy= 22.22.22.22/255.255.255.255/47/0
026042: Mar 17 01:05:16.830: ISAKMP: Failed to find peer index node to update peer_info_list
026043: Mar 17 01:05:16.830: ISAKMP:(2024):Received IPSec Install callback... proceeding with the negotiation
026044: Mar 17 01:05:16.830: ISAKMP:(2024):Successfully installed IPSEC SA (SPI:0x7B2235E) on Dialer1
026045: Mar 17 01:05:16.830: ISAKMP:(2024): sending packet to 22.22.22.22 my_port 500 peer_port 500 (R) QM_IDLE
026046: Mar 17 01:05:16.830: ISAKMP:(2024):Sending an IKE IPv4 Packet.
026047: Mar 17 01:05:16.830: ISAKMP:(2024):Node 1882507048, Input = IKE_MESG_FROM_IPSEC, IPSEC_INSTALL_DONE
026048: Mar 17 01:05:16.830: ISAKMP:(2024):Old State = IKE_QM_IPSEC_INSTALL_AWAIT New State = IKE_QM_R_QM2
026049: Mar 17 01:05:16.850: ISAKMP (2024): received packet from 22.22.22.22 dport 500 sport 500 Global (R) QM_IDLE
026050: Mar 17 01:05:16.850: ISAKMP:(2024):deleting node 1882507048 error FALSE reason "QM done (await)"
026051: Mar 17 01:05:16.850: ISAKMP:(2024):Node 1882507048, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
026052: Mar 17 01:05:16.850: ISAKMP:(2024):Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE
RT-1#
RT-2のデバッグログ(イニシエーターとして動作)
RT-2#
019197: Mar 17 01:05:16.841: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 22.22.22.22:500, remote= 11.11.11.11:500,
local_proxy= 22.22.22.22/255.255.255.255/47/0,
remote_proxy= 11.11.11.11/255.255.255.255/47/0,
protocol= ESP, transform= esp-aes esp-sha256-hmac (Transport),
lifedur= 1200s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
019198: Mar 17 01:05:16.841: ISAKMP:(0): SA request profile is (NULL)
019199: Mar 17 01:05:16.841: ISAKMP: Created a peer struct for 11.11.11.11, peer port 500
019200: Mar 17 01:05:16.841: ISAKMP: New peer created peer = 0x1EAD604 peer_handle = 0x8000000B
019201: Mar 17 01:05:16.841: ISAKMP: Locking peer struct 0x1EAD604, refcount 1 for isakmp_initiator
019202: Mar 17 01:05:16.841: ISAKMP: local port 500, remote port 500
019203: Mar 17 01:05:16.841: ISAKMP: set new node 0 to QM_IDLE
019204: Mar 17 01:05:16.841: ISAKMP: Find a dup sa in the avl tree during calling isadb_insert sa = 1246715C
019205: Mar 17 01:05:16.841: ISAKMP:(0):Can not start Aggressive mode, trying Main mode.
019206: Mar 17 01:05:16.841: ISAKMP:(0):found peer pre-shared key matching 11.11.11.11
019207: Mar 17 01:05:16.841: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID
019208: Mar 17 01:05:16.841: ISAKMP:(0): constructed NAT-T vendor-07 ID
019209: Mar 17 01:05:16.841: ISAKMP:(0): constructed NAT-T vendor-03 ID
019210: Mar 17 01:05:16.841: ISAKMP:(0): constructed NAT-T vendor-02 ID
019211: Mar 17 01:05:16.841: ISAKMP:(0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
019212: Mar 17 01:05:16.841: ISAKMP:(0):Old State = IKE_READY New State = IKE_I_MM1
019213: Mar 17 01:05:16.841: ISAKMP:(0): beginning Main Mode exchange
019214: Mar 17 01:05:16.841: ISAKMP:(0): sending packet to 11.11.11.11 my_port 500 peer_port 500 (I) MM_NO_STATE
019215: Mar 17 01:05:16.841: ISAKMP:(0):Sending an IKE IPv4 Packet.
019216: Mar 17 01:05:16.845: ISAKMP (0): received packet from 11.11.11.11 dport 500 sport 500 Global (I) MM_NO_STATE
019217: Mar 17 01:05:16.845: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
019218: Mar 17 01:05:16.845: ISAKMP:(0):Old State = IKE_I_MM1 New State = IKE_I_MM2
019219: Mar 17 01:05:16.845: ISAKMP:(0): processing SA payload. message ID = 0
019220: Mar 17 01:05:16.845: ISAKMP:(0): processing vendor id payload
019221: Mar 17 01:05:16.845: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
019222: Mar 17 01:05:16.845: ISAKMP (0): vendor ID is NAT-T RFC 3947
019223: Mar 17 01:05:16.845: ISAKMP:(0):found peer pre-shared key matching 11.11.11.11
019224: Mar 17 01:05:16.845: ISAKMP:(0): local preshared key found
019225: Mar 17 01:05:16.845: ISAKMP : Scanning profiles for xauth ...
019226: Mar 17 01:05:16.845: ISAKMP:(0):Checking ISAKMP transform 1 against priority 110 policy
019227: Mar 17 01:05:16.845: ISAKMP: encryption AES-CBC
019228: Mar 17 01:05:16.845: ISAKMP: keylength of 128
019229: Mar 17 01:05:16.845: ISAKMP: hash SHA256
019230: Mar 17 01:05:16.845: ISAKMP: default group 2
019231: Mar 17 01:05:16.845: ISAKMP: auth pre-share
019232: Mar 17 01:05:16.845: ISAKMP: life type in seconds
019233: Mar 17 01:05:16.845: ISAKMP: life duration (basic) of 1800
019234: Mar 17 01:05:16.845: ISAKMP:(0):atts are acceptable. Next payload is 0
019235: Mar 17 01:05:16.845: ISAKMP:(0):Acceptable atts:actual life: 0
019236: Mar 17 01:05:16.845: ISAKMP:(0):Acceptable atts:life: 0
019237: Mar 17 01:05:16.845: ISAKMP:(0):Basic life_in_seconds:1800
019238: Mar 17 01:05:16.845: ISAKMP:(0):Returning Actual lifetime: 1800
019239: Mar 17 01:05:16.845: ISAKMP:(0)::Started lifetime timer: 1800.
019240: Mar 17 01:05:16.845: ISAKMP:(0): processing vendor id payload
019241: Mar 17 01:05:16.845: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
019242: Mar 17 01:05:16.845: ISAKMP (0): vendor ID is NAT-T RFC 3947
019243: Mar 17 01:05:16.845: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
019244: Mar 17 01:05:16.845: ISAKMP:(0):Old State = IKE_I_MM2 New State = IKE_I_MM2
019245: Mar 17 01:05:16.845: ISAKMP:(0): sending packet to 11.11.11.11 my_port 500 peer_port 500 (I) MM_SA_SETUP
019246: Mar 17 01:05:16.845: ISAKMP:(0):Sending an IKE IPv4 Packet.
019247: Mar 17 01:05:16.845: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
019248: Mar 17 01:05:16.845: ISAKMP:(0):Old State = IKE_I_MM2 New State = IKE_I_MM3
019249: Mar 17 01:05:16.853: ISAKMP (0): received packet from 11.11.11.11 dport 500 sport 500 Global (I) MM_SA_SETUP
019250: Mar 17 01:05:16.853: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
019251: Mar 17 01:05:16.853: ISAKMP:(0):Old State = IKE_I_MM3 New State = IKE_I_MM4
019252: Mar 17 01:05:16.853: ISAKMP:(0): processing KE payload. message ID = 0
019253: Mar 17 01:05:16.857: ISAKMP:(0): processing NONCE payload. message ID = 0
019254: Mar 17 01:05:16.857: ISAKMP:(0):found peer pre-shared key matching 11.11.11.11
019255: Mar 17 01:05:16.857: ISAKMP:(2024): processing vendor id payload
019256: Mar 17 01:05:16.857: ISAKMP:(2024): vendor ID is Unity
019257: Mar 17 01:05:16.857: ISAKMP:(2024): processing vendor id payload
019258: Mar 17 01:05:16.857: ISAKMP:(2024): vendor ID is DPD
019259: Mar 17 01:05:16.857: ISAKMP:(2024): processing vendor id payload
019260: Mar 17 01:05:16.857: ISAKMP:(2024): speaking to another IOS box!
019261: Mar 17 01:05:16.857: ISAKMP:received payload type 20
019262: Mar 17 01:05:16.857: ISAKMP (2024): His hash no match - this node outside NAT
019263: Mar 17 01:05:16.857: ISAKMP:received payload type 20
019264: Mar 17 01:05:16.857: ISAKMP (2024): No NAT Found for self or peer
019265: Mar 17 01:05:16.857: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
019266: Mar 17 01:05:16.857: ISAKMP:(2024):Old State = IKE_I_MM4 New State = IKE_I_MM4
019267: Mar 17 01:05:16.857: ISAKMP:(2024):Send initial contact
019268: Mar 17 01:05:16.857: ISAKMP:(2024):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
019269: Mar 17 01:05:16.857: ISAKMP (2024): ID payload
next-payload : 8
type : 1
address : 22.22.22.22
protocol : 17
port : 500
length : 12
019270: Mar 17 01:05:16.857: ISAKMP:(2024):Total payload length: 12
019271: Mar 17 01:05:16.857: ISAKMP:(2024): sending packet to 11.11.11.11 my_port 500 peer_port 500 (I) MM_KEY_EXCH
019272: Mar 17 01:05:16.857: ISAKMP:(2024):Sending an IKE IPv4 Packet.
019273: Mar 17 01:05:16.857: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
019274: Mar 17 01:05:16.857: ISAKMP:(2024):Old State = IKE_I_MM4 New State = IKE_I_MM5
019275: Mar 17 01:05:16.861: ISAKMP (2024): received packet from 11.11.11.11 dport 500 sport 500 Global (I) MM_KEY_EXCH
019276: Mar 17 01:05:16.861: ISAKMP:(2024): processing ID payload. message ID = 0
019277: Mar 17 01:05:16.861: ISAKMP (2024): ID payload
next-payload : 8
type : 1
address : 11.11.11.11
protocol : 17
port : 500
length : 12
019278: Mar 17 01:05:16.861: ISAKMP:(0):: peer matches *none* of the profiles
019279: Mar 17 01:05:16.861: ISAKMP:(2024): processing HASH payload. message ID = 0
019280: Mar 17 01:05:16.861: ISAKMP:(2024):SA authentication status:
authenticated
019281: Mar 17 01:05:16.861: ISAKMP:(2024):SA has been authenticated with 11.11.11.11
019282: Mar 17 01:05:16.861: ISAKMP: Trying to insert a peer 22.22.22.22/11.11.11.11/500/, and inserted successfully 1EAD604.
019283: Mar 17 01:05:16.861: ISAKMP:(2024):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
019284: Mar 17 01:05:16.861: ISAKMP:(2024):Old State = IKE_I_MM5 New State = IKE_I_MM6
019285: Mar 17 01:05:16.861: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
019286: Mar 17 01:05:16.861: ISAKMP:(2024):Old State = IKE_I_MM6 New State = IKE_I_MM6
019287: Mar 17 01:05:16.861: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
019288: Mar 17 01:05:16.861: ISAKMP:(2024):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
019289: Mar 17 01:05:16.861: ISAKMP:(2024):IKE_DPD is enabled, initializing timers
019290: Mar 17 01:05:16.861: ISAKMP:(2024):beginning Quick Mode exchange, M-ID of 1882507048
019291: Mar 17 01:05:16.861: ISAKMP:(2024):QM Initiator gets spi
019292: Mar 17 01:05:16.861: ISAKMP:(2024): sending packet to 11.11.11.11 my_port 500 peer_port 500 (I) QM_IDLE
019293: Mar 17 01:05:16.861: ISAKMP:(2024):Sending an IKE IPv4 Packet.
019294: Mar 17 01:05:16.865: ISAKMP:(2024):Node 1882507048, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
019295: Mar 17 01:05:16.865: ISAKMP:(2024):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
019296: Mar 17 01:05:16.865: ISAKMP:(2024):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
019297: Mar 17 01:05:16.865: ISAKMP:(2024):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
019298: Mar 17 01:05:16.881: ISAKMP (2024): received packet from 11.11.11.11 dport 500 sport 500 Global (I) QM_IDLE
019299: Mar 17 01:05:16.881: ISAKMP:(2024): processing HASH payload. message ID = 1882507048
019300: Mar 17 01:05:16.881: ISAKMP:(2024): processing SA payload. message ID = 1882507048
019301: Mar 17 01:05:16.881: ISAKMP:(2024):Checking IPSec proposal 1
019302: Mar 17 01:05:16.881: ISAKMP: transform 1, ESP_AES
019303: Mar 17 01:05:16.881: ISAKMP: attributes in transform:
019304: Mar 17 01:05:16.881: ISAKMP: encaps is 2 (Transport)
019305: Mar 17 01:05:16.881: ISAKMP: SA life type in seconds
019306: Mar 17 01:05:16.881: ISAKMP: SA life duration (basic) of 1200
019307: Mar 17 01:05:16.881: ISAKMP: SA life type in kilobytes
019308: Mar 17 01:05:16.881: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
019309: Mar 17 01:05:16.881: ISAKMP: authenticator is HMAC-SHA256
019310: Mar 17 01:05:16.881: ISAKMP: key length is 128
019311: Mar 17 01:05:16.881: ISAKMP: group is 14
019312: Mar 17 01:05:16.881: ISAKMP:(2024):atts are acceptable.
019313: Mar 17 01:05:16.881: IPSEC(validate_proposal_request): proposal part #1
019314: Mar 17 01:05:16.881: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 22.22.22.22/255.255.255.255/47/0,
remote_proxy= 11.11.11.11/255.255.255.255/47/0,
protocol= ESP, transform= NONE (Transport),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
019315: Mar 17 01:05:16.881: Crypto mapdb : proxy_match
src addr : 22.22.22.22
dst addr : 11.11.11.11
protocol : 47
src port : 0
dst port : 0
019316: Mar 17 01:05:16.881: (ipsec_process_proposal)Map Accepted: MAP-name, 160
019317: Mar 17 01:05:16.881: ISAKMP:(2024): processing NONCE payload. message ID = 1882507048
019318: Mar 17 01:05:16.881: ISAKMP:(2024): processing KE payload. message ID = 1882507048
019319: Mar 17 01:05:16.897: ISAKMP:(2024): processing ID payload. message ID = 1882507048
019320: Mar 17 01:05:16.897: ISAKMP:(2024): processing ID payload. message ID = 1882507048
019321: Mar 17 01:05:16.897: ISAKMP:(2024):Node 1882507048, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
019322: Mar 17 01:05:16.897: ISAKMP:(2024):Old State = IKE_QM_I_QM1 New State = IKE_QM_IPSEC_INSTALL_AWAIT
019323: Mar 17 01:05:16.897: IPSEC(key_engine): got a queue event with 1 KMI message(s)
019324: Mar 17 01:05:16.897: Crypto mapdb : proxy_match
src addr : 22.22.22.22
dst addr : 11.11.11.11
protocol : 47
src port : 0
dst port : 0
019325: Mar 17 01:05:16.897: IPSEC(crypto_ipsec_create_ipsec_sas): Map found MAP-name, 160
019326: Mar 17 01:05:16.897: IPSEC(create_sa): sa created,
(sa) sa_dest= 22.22.22.22, sa_proto= 50,
sa_spi= 0x259C42D3(630997715),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 57
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 22.22.22.22/255.255.255.255/47/0,
remote_proxy= 11.11.11.11/255.255.255.255/47/0
019327: Mar 17 01:05:16.897: IPSEC(create_sa): sa created,
(sa) sa_dest= 11.11.11.11, sa_proto= 50,
sa_spi= 0x7B2235E(129114974),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 58
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 22.22.22.22/255.255.255.255/47/0,
remote_proxy= 11.11.11.11/255.255.255.255/47/0
019328: Mar 17 01:05:16.897: IPSEC: Expand action denied, notify RP
019329: Mar 17 01:05:16.897: ISAKMP: Failed to find peer index node to update peer_info_list
019330: Mar 17 01:05:16.897: ISAKMP:(2024):Received IPSec Install callback... proceeding with the negotiation
019331: Mar 17 01:05:16.897: ISAKMP:(2024):Successfully installed IPSEC SA (SPI:0x259C42D3) on Dialer1
019332: Mar 17 01:05:16.897: ISAKMP:(2024): sending packet to 11.11.11.11 my_port 500 peer_port 500 (I) QM_IDLE
019333: Mar 17 01:05:16.897: ISAKMP:(2024):Sending an IKE IPv4 Packet.
019334: Mar 17 01:05:16.897: ISAKMP:(2024):deleting node 1882507048 error FALSE reason "No Error"
019335: Mar 17 01:05:16.897: ISAKMP:(2024):Node 1882507048, Input = IKE_MESG_FROM_IPSEC, IPSEC_INSTALL_DONE
019336: Mar 17 01:05:16.897: ISAKMP:(2024):Old State = IKE_QM_IPSEC_INSTALL_AWAIT New State = IKE_QM_PHASE2_COMPLETE
RT-2#
