Cisco
サイト間IPsecのデバッグログ
構成図
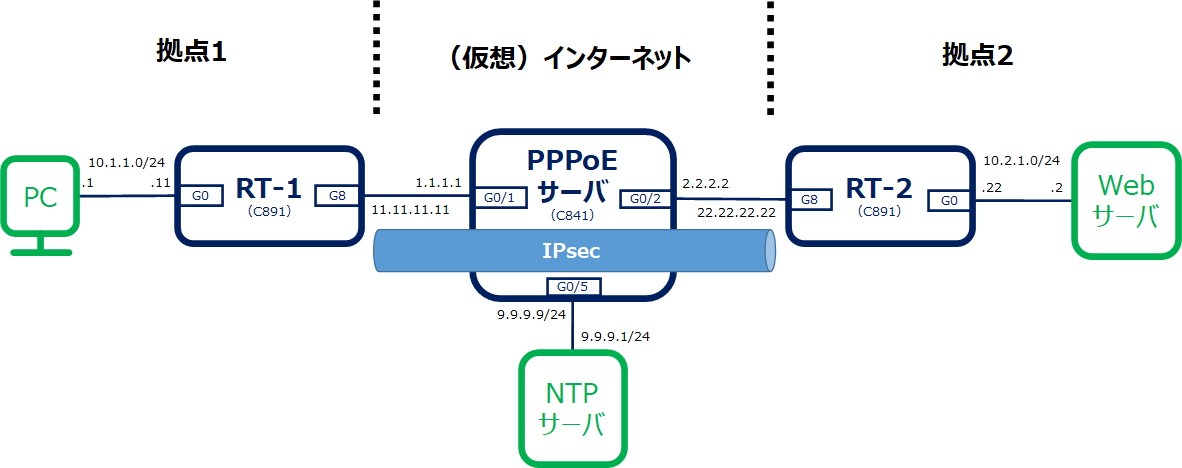
IPsec+PPPoE+NAT+ACLのコンフィグで、IPsecが接続される際のデバッグログを記録します。
RT-1のデバッグログ(イニシエーターとして動作)
RT-1#terminal monitor
RT-1#
RT-1#debug crypto isakmp
Crypto ISAKMP debugging is on
RT-1#
RT-1#debug crypto ipsec
Crypto IPSEC debugging is on
RT-1#
000043: Nov 10 20:54:09.642: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 11.11.11.11:500, remote= 22.22.22.22:500,
local_proxy= 10.1.1.0/255.255.255.0/256/0,
remote_proxy= 10.2.1.0/255.255.255.0/256/0,
protocol= ESP, transform= esp-aes esp-sha256-hmac (Tunnel),
lifedur= 1200s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
000044: Nov 10 20:54:09.642: ISAKMP:(0): SA request profile is (NULL)
000045: Nov 10 20:54:09.642: ISAKMP: Created a peer struct for 22.22.22.22, peer port 500
000046: Nov 10 20:54:09.642: ISAKMP: New peer created peer = 0x2421644 peer_handle = 0x80000002
000047: Nov 10 20:54:09.642: ISAKMP: Locking peer struct 0x2421644, refcount 1 for isakmp_initiator
000048: Nov 10 20:54:09.646: ISAKMP: local port 500, remote port 500
000049: Nov 10 20:54:09.646: ISAKMP: set new node 0 to QM_IDLE
000050: Nov 10 20:54:09.646: ISAKMP:(0):insert sa successfully sa = 101371C
000051: Nov 10 20:54:09.646: ISAKMP:(0):Can not start Aggressive mode, trying Main mode.
000052: Nov 10 20:54:09.646: ISAKMP:(0):found peer pre-shared key matching 22.22.22.22
000053: Nov 10 20:54:09.646: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID
000054: Nov 10 20:54:09.646: ISAKMP:(0): constructed NAT-T vendor-07 ID
000055: Nov 10 20:54:09.646: ISAKMP:(0): constructed NAT-T vendor-03 ID
000056: Nov 10 20:54:09.646: ISAKMP:(0): constructed NAT-T vendor-02 ID
000057: Nov 10 20:54:09.646: ISAKMP:(0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
000058: Nov 10 20:54:09.646: ISAKMP:(0):Old State = IKE_READY New State = IKE_I_MM1
000059: Nov 10 20:54:09.646: ISAKMP:(0): beginning Main Mode exchange
000060: Nov 10 20:54:09.646: ISAKMP:(0): sending packet to 22.22.22.22 my_port 500 peer_port 500 (I) MM_NO_STATE
000061: Nov 10 20:54:09.646: ISAKMP:(0):Sending an IKE IPv4 Packet.
000062: Nov 10 20:54:09.650: ISAKMP (0): received packet from 22.22.22.22 dport 500 sport 500 Global (I) MM_NO_STATE
000063: Nov 10 20:54:09.650: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
000064: Nov 10 20:54:09.650: ISAKMP:(0):Old State = IKE_I_MM1 New State = IKE_I_MM2
000065: Nov 10 20:54:09.650: ISAKMP:(0): processing SA payload. message ID = 0
000066: Nov 10 20:54:09.650: ISAKMP:(0): processing vendor id payload
000067: Nov 10 20:54:09.650: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
000068: Nov 10 20:54:09.650: ISAKMP (0): vendor ID is NAT-T RFC 3947
000069: Nov 10 20:54:09.650: ISAKMP:(0):found peer pre-shared key matching 22.22.22.22
000070: Nov 10 20:54:09.650: ISAKMP:(0): local preshared key found
000071: Nov 10 20:54:09.650: ISAKMP : Scanning profiles for xauth ...
000072: Nov 10 20:54:09.650: ISAKMP:(0):Checking ISAKMP transform 1 against priority 110 policy
000073: Nov 10 20:54:09.650: ISAKMP: encryption AES-CBC
000074: Nov 10 20:54:09.650: ISAKMP: keylength of 128
000075: Nov 10 20:54:09.650: ISAKMP: hash SHA256
000076: Nov 10 20:54:09.650: ISAKMP: default group 2
000077: Nov 10 20:54:09.650: ISAKMP: auth pre-share
000078: Nov 10 20:54:09.650: ISAKMP: life type in seconds
000079: Nov 10 20:54:09.650: ISAKMP: life duration (basic) of 1800
000080: Nov 10 20:54:09.650: ISAKMP:(0):atts are acceptable. Next payload is 0
000081: Nov 10 20:54:09.650: ISAKMP:(0):Acceptable atts:actual life: 0
000082: Nov 10 20:54:09.650: ISAKMP:(0):Acceptable atts:life: 0
000083: Nov 10 20:54:09.650: ISAKMP:(0):Basic life_in_seconds:1800
000084: Nov 10 20:54:09.650: ISAKMP:(0):Returning Actual lifetime: 1800
000085: Nov 10 20:54:09.650: ISAKMP:(0)::Started lifetime timer: 1800.
000086: Nov 10 20:54:09.650: ISAKMP:(0): processing vendor id payload
000087: Nov 10 20:54:09.650: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
000088: Nov 10 20:54:09.650: ISAKMP (0): vendor ID is NAT-T RFC 3947
000089: Nov 10 20:54:09.650: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
000090: Nov 10 20:54:09.650: ISAKMP:(0):Old State = IKE_I_MM2 New State = IKE_I_MM2
000091: Nov 10 20:54:09.650: ISAKMP:(0): sending packet to 22.22.22.22 my_port 500 peer_port 500 (I) MM_SA_SETUP
000092: Nov 10 20:54:09.650: ISAKMP:(0):Sending an IKE IPv4 Packet.
000093: Nov 10 20:54:09.650: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
000094: Nov 10 20:54:09.650: ISAKMP:(0):Old State = IKE_I_MM2 New State = IKE_I_MM3
000095: Nov 10 20:54:09.658: ISAKMP (0): received packet from 22.22.22.22 dport 500 sport 500 Global (I) MM_SA_SETUP
000096: Nov 10 20:54:09.658: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
000097: Nov 10 20:54:09.658: ISAKMP:(0):Old State = IKE_I_MM3 New State = IKE_I_MM4
000098: Nov 10 20:54:09.658: ISAKMP:(0): processing KE payload. message ID = 0
000099: Nov 10 20:54:09.662: ISAKMP:(0): processing NONCE payload. message ID = 0
000100: Nov 10 20:54:09.662: ISAKMP:(0):found peer pre-shared key matching 22.22.22.22
000101: Nov 10 20:54:09.662: ISAKMP:(2001): processing vendor id payload
000102: Nov 10 20:54:09.662: ISAKMP:(2001): vendor ID is Unity
000103: Nov 10 20:54:09.662: ISAKMP:(2001): processing vendor id payload
000104: Nov 10 20:54:09.662: ISAKMP:(2001): vendor ID is DPD
000105: Nov 10 20:54:09.662: ISAKMP:(2001): processing vendor id payload
000106: Nov 10 20:54:09.662: ISAKMP:(2001): speaking to another IOS box!
000107: Nov 10 20:54:09.662: ISAKMP:received payload type 20
000108: Nov 10 20:54:09.662: ISAKMP (2001): His hash no match - this node outside NAT
000109: Nov 10 20:54:09.662: ISAKMP:received payload type 20
000110: Nov 10 20:54:09.662: ISAKMP (2001): No NAT Found for self or peer
000111: Nov 10 20:54:09.662: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
000112: Nov 10 20:54:09.662: ISAKMP:(2001):Old State = IKE_I_MM4 New State = IKE_I_MM4
000113: Nov 10 20:54:09.662: ISAKMP:(2001):Send initial contact
000114: Nov 10 20:54:09.662: ISAKMP:(2001):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
000115: Nov 10 20:54:09.662: ISAKMP (2001): ID payload
next-payload : 8
type : 1
address : 11.11.11.11
protocol : 17
port : 500
length : 12
000116: Nov 10 20:54:09.662: ISAKMP:(2001):Total payload length: 12
000117: Nov 10 20:54:09.662: ISAKMP:(2001): sending packet to 22.22.22.22 my_port 500 peer_port 500 (I) MM_KEY_EXCH
000118: Nov 10 20:54:09.662: ISAKMP:(2001):Sending an IKE IPv4 Packet.
000119: Nov 10 20:54:09.662: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
000120: Nov 10 20:54:09.662: ISAKMP:(2001):Old State = IKE_I_MM4 New State = IKE_I_MM5
000121: Nov 10 20:54:09.666: ISAKMP (2001): received packet from 22.22.22.22 dport 500 sport 500 Global (I) MM_KEY_EXCH
000122: Nov 10 20:54:09.666: ISAKMP:(2001): processing ID payload. message ID = 0
000123: Nov 10 20:54:09.666: ISAKMP (2001): ID payload
next-payload : 8
type : 1
address : 22.22.22.22
protocol : 17
port : 500
length : 12
000124: Nov 10 20:54:09.666: ISAKMP:(0):: peer matches *none* of the profiles
000125: Nov 10 20:54:09.666: ISAKMP:(2001): processing HASH payload. message ID = 0
000126: Nov 10 20:54:09.666: ISAKMP:(2001):SA authentication status:
authenticated
000127: Nov 10 20:54:09.666: ISAKMP:(2001):SA has been authenticated with 22.22.22.22
000128: Nov 10 20:54:09.666: ISAKMP: Trying to insert a peer 11.11.11.11/22.22.22.22/500/, and inserted successfully 2421644.
000129: Nov 10 20:54:09.666: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
000130: Nov 10 20:54:09.666: ISAKMP:(2001):Old State = IKE_I_MM5 New State = IKE_I_MM6
000131: Nov 10 20:54:09.666: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
000132: Nov 10 20:54:09.666: ISAKMP:(2001):Old State = IKE_I_MM6 New State = IKE_I_MM6
000133: Nov 10 20:54:09.670: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
000134: Nov 10 20:54:09.670: ISAKMP:(2001):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
000135: Nov 10 20:54:09.670: ISAKMP:(2001):IKE_DPD is enabled, initializing timers
000136: Nov 10 20:54:09.670: ISAKMP:(2001):beginning Quick Mode exchange, M-ID of 2126720465
000137: Nov 10 20:54:09.670: ISAKMP:(2001):QM Initiator gets spi
000138: Nov 10 20:54:09.670: ISAKMP:(2001): sending packet to 22.22.22.22 my_port 500 peer_port 500 (I) QM_IDLE
000139: Nov 10 20:54:09.670: ISAKMP:(2001):Sending an IKE IPv4 Packet.
000140: Nov 10 20:54:09.670: ISAKMP:(2001):Node 2126720465, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
000141: Nov 10 20:54:09.670: ISAKMP:(2001):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
000142: Nov 10 20:54:09.670: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
000143: Nov 10 20:54:09.670: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
000144: Nov 10 20:54:09.686: ISAKMP (2001): received packet from 22.22.22.22 dport 500 sport 500 Global (I) QM_IDLE
000145: Nov 10 20:54:09.686: ISAKMP:(2001): processing HASH payload. message ID = 2126720465
000146: Nov 10 20:54:09.686: ISAKMP:(2001): processing SA payload. message ID = 2126720465
000147: Nov 10 20:54:09.686: ISAKMP:(2001):Checking IPSec proposal 1
000148: Nov 10 20:54:09.686: ISAKMP: transform 1, ESP_AES
000149: Nov 10 20:54:09.686: ISAKMP: attributes in transform:
000150: Nov 10 20:54:09.686: ISAKMP: encaps is 1 (Tunnel)
000151: Nov 10 20:54:09.686: ISAKMP: SA life type in seconds
000152: Nov 10 20:54:09.690: ISAKMP: SA life duration (basic) of 1200
000153: Nov 10 20:54:09.690: ISAKMP: SA life type in kilobytes
000154: Nov 10 20:54:09.690: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
000155: Nov 10 20:54:09.690: ISAKMP: authenticator is HMAC-SHA256
000156: Nov 10 20:54:09.690: ISAKMP: key length is 128
000157: Nov 10 20:54:09.690: ISAKMP: group is 14
000158: Nov 10 20:54:09.690: ISAKMP:(2001):atts are acceptable.
000159: Nov 10 20:54:09.690: IPSEC(validate_proposal_request): proposal part #1
000160: Nov 10 20:54:09.690: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 10.1.1.0/255.255.255.0/256/0,
remote_proxy= 10.2.1.0/255.255.255.0/256/0,
protocol= ESP, transform= NONE (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
000161: Nov 10 20:54:09.690: Crypto mapdb : proxy_match
src addr : 10.1.1.0
dst addr : 10.2.1.0
protocol : 0
src port : 0
dst port : 0
000162: Nov 10 20:54:09.690: (ipsec_process_proposal)Map Accepted: MAP-name, 160
000163: Nov 10 20:54:09.690: ISAKMP:(2001): processing NONCE payload. message ID = 2126720465
000164: Nov 10 20:54:09.690: ISAKMP:(2001): processing KE payload. message ID = 2126720465
000165: Nov 10 20:54:09.702: ISAKMP:(2001): processing ID payload. message ID = 2126720465
000166: Nov 10 20:54:09.702: ISAKMP:(2001): processing ID payload. message ID = 2126720465
000167: Nov 10 20:54:09.702: ISAKMP:(2001):Node 2126720465, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
000168: Nov 10 20:54:09.702: ISAKMP:(2001):Old State = IKE_QM_I_QM1 New State = IKE_QM_IPSEC_INSTALL_AWAIT
000169: Nov 10 20:54:09.702: IPSEC(key_engine): got a queue event with 1 KMI message(s)
000170: Nov 10 20:54:09.702: Crypto mapdb : proxy_match
src addr : 10.1.1.0
dst addr : 10.2.1.0
protocol : 256
src port : 0
dst port : 0
000171: Nov 10 20:54:09.702: IPSEC(crypto_ipsec_create_ipsec_sas): Map found MAP-name, 160
000172: Nov 10 20:54:09.702: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and peer 22.22.22.22
000173: Nov 10 20:54:09.702: IPSEC(create_sa): sa created,
(sa) sa_dest= 11.11.11.11, sa_proto= 50,
sa_spi= 0x3C27C1A1(1009238433),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 1
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 10.1.1.0/255.255.255.0/256/0,
remote_proxy= 10.2.1.0/255.255.255.0/256/0
000174: Nov 10 20:54:09.702: IPSEC(create_sa): sa created,
(sa) sa_dest= 22.22.22.22, sa_proto= 50,
sa_spi= 0xAC6FE00C(2893013004),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 2
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 10.1.1.0/255.255.255.0/256/0,
remote_proxy= 10.2.1.0/255.255.255.0/256/0
000175: Nov 10 20:54:09.702: IPSEC: Expand action denied, notify RP
000176: Nov 10 20:54:09.702: ISAKMP: Failed to find peer index node to update peer_info_list
000177: Nov 10 20:54:09.702: ISAKMP:(2001):Received IPSec Install callback... proceeding with the negotiation
000178: Nov 10 20:54:09.702: ISAKMP:(2001):Successfully installed IPSEC SA (SPI:0x3C27C1A1) on Dialer1
000179: Nov 10 20:54:09.702: ISAKMP:(2001): sending packet to 22.22.22.22 my_port 500 peer_port 500 (I) QM_IDLE
000180: Nov 10 20:54:09.702: ISAKMP:(2001):Sending an IKE IPv4 Packet.
RT-1#
000181: Nov 10 20:54:09.702: ISAKMP:(2001):deleting node 2126720465 error FALSE reason "No Error"
000182: Nov 10 20:54:09.702: ISAKMP:(2001):Node 2126720465, Input = IKE_MESG_FROM_IPSEC, IPSEC_INSTALL_DONE
000183: Nov 10 20:54:09.702: ISAKMP:(2001):Old State = IKE_QM_IPSEC_INSTALL_AWAIT New State = IKE_QM_PHASE2_COMPLETE
RT-1#
RT-1#no debug all
All possible debugging has been turned off
RT-1#
RT-2のデバッグログ(レスポンダーとして動作)
RT-2#debug crypto isakmp
Crypto ISAKMP debugging is on
RT-2#
RT-2#debug crypto ipsec
Crypto IPSEC debugging is on
RT-2#
000056: Nov 10 20:54:09.647: ISAKMP (0): received packet from 11.11.11.11 dport 500 sport 500 Global (N) NEW SA
000057: Nov 10 20:54:09.647: ISAKMP: Created a peer struct for 11.11.11.11, peer port 500
000058: Nov 10 20:54:09.647: ISAKMP: New peer created peer = 0x3410964 peer_handle = 0x80000002
000059: Nov 10 20:54:09.647: ISAKMP: Locking peer struct 0x3410964, refcount 1 for crypto_isakmp_process_block
000060: Nov 10 20:54:09.647: ISAKMP: local port 500, remote port 500
000061: Nov 10 20:54:09.647: ISAKMP:(0):insert sa successfully sa = 1046561C
000062: Nov 10 20:54:09.647: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
000063: Nov 10 20:54:09.647: ISAKMP:(0):Old State = IKE_READY New State = IKE_R_MM1
000064: Nov 10 20:54:09.651: ISAKMP:(0): processing SA payload. message ID = 0
000065: Nov 10 20:54:09.651: ISAKMP:(0): processing vendor id payload
000066: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
000067: Nov 10 20:54:09.651: ISAKMP (0): vendor ID is NAT-T RFC 3947
000068: Nov 10 20:54:09.651: ISAKMP:(0): processing vendor id payload
000069: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID seems Unity/DPD but major 245 mismatch
000070: Nov 10 20:54:09.651: ISAKMP (0): vendor ID is NAT-T v7
000071: Nov 10 20:54:09.651: ISAKMP:(0): processing vendor id payload
000072: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID seems Unity/DPD but major 157 mismatch
000073: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID is NAT-T v3
000074: Nov 10 20:54:09.651: ISAKMP:(0): processing vendor id payload
000075: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
000076: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID is NAT-T v2
000077: Nov 10 20:54:09.651: ISAKMP:(0):found peer pre-shared key matching 11.11.11.11
000078: Nov 10 20:54:09.651: ISAKMP:(0): local preshared key found
000079: Nov 10 20:54:09.651: ISAKMP : Scanning profiles for xauth ...
000080: Nov 10 20:54:09.651: ISAKMP:(0):Checking ISAKMP transform 1 against priority 110 policy
000081: Nov 10 20:54:09.651: ISAKMP: encryption AES-CBC
000082: Nov 10 20:54:09.651: ISAKMP: keylength of 128
000083: Nov 10 20:54:09.651: ISAKMP: hash SHA256
000084: Nov 10 20:54:09.651: ISAKMP: default group 2
000085: Nov 10 20:54:09.651: ISAKMP: auth pre-share
000086: Nov 10 20:54:09.651: ISAKMP: life type in seconds
000087: Nov 10 20:54:09.651: ISAKMP: life duration (basic) of 1800
000088: Nov 10 20:54:09.651: ISAKMP:(0):atts are acceptable. Next payload is 0
000089: Nov 10 20:54:09.651: ISAKMP:(0):Acceptable atts:actual life: 1800
000090: Nov 10 20:54:09.651: ISAKMP:(0):Acceptable atts:life: 0
000091: Nov 10 20:54:09.651: ISAKMP:(0):Basic life_in_seconds:1800
000092: Nov 10 20:54:09.651: ISAKMP:(0):Returning Actual lifetime: 1800
000093: Nov 10 20:54:09.651: ISAKMP:(0)::Started lifetime timer: 1800.
000094: Nov 10 20:54:09.651: ISAKMP:(0): processing vendor id payload
000095: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
000096: Nov 10 20:54:09.651: ISAKMP (0): vendor ID is NAT-T RFC 3947
000097: Nov 10 20:54:09.651: ISAKMP:(0): processing vendor id payload
000098: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID seems Unity/DPD but major 245 mismatch
000099: Nov 10 20:54:09.651: ISAKMP (0): vendor ID is NAT-T v7
000100: Nov 10 20:54:09.651: ISAKMP:(0): processing vendor id payload
000101: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID seems Unity/DPD but major 157 mismatch
000102: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID is NAT-T v3
000103: Nov 10 20:54:09.651: ISAKMP:(0): processing vendor id payload
000104: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
000105: Nov 10 20:54:09.651: ISAKMP:(0): vendor ID is NAT-T v2
000106: Nov 10 20:54:09.651: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
000107: Nov 10 20:54:09.651: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM1
000108: Nov 10 20:54:09.651: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID
000109: Nov 10 20:54:09.651: ISAKMP:(0): sending packet to 11.11.11.11 my_port 500 peer_port 500 (R) MM_SA_SETUP
000110: Nov 10 20:54:09.651: ISAKMP:(0):Sending an IKE IPv4 Packet.
000111: Nov 10 20:54:09.651: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
000112: Nov 10 20:54:09.651: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM2
000113: Nov 10 20:54:09.655: ISAKMP (0): received packet from 11.11.11.11 dport 500 sport 500 Global (R) MM_SA_SETUP
000114: Nov 10 20:54:09.655: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
000115: Nov 10 20:54:09.655: ISAKMP:(0):Old State = IKE_R_MM2 New State = IKE_R_MM3
000116: Nov 10 20:54:09.655: ISAKMP:(0): processing KE payload. message ID = 0
000117: Nov 10 20:54:09.659: ISAKMP:(0): processing NONCE payload. message ID = 0
000118: Nov 10 20:54:09.659: ISAKMP:(0):found peer pre-shared key matching 11.11.11.11
000119: Nov 10 20:54:09.659: ISAKMP:(2001): processing vendor id payload
000120: Nov 10 20:54:09.659: ISAKMP:(2001): vendor ID is DPD
000121: Nov 10 20:54:09.659: ISAKMP:(2001): processing vendor id payload
000122: Nov 10 20:54:09.659: ISAKMP:(2001): speaking to another IOS box!
000123: Nov 10 20:54:09.659: ISAKMP:(2001): processing vendor id payload
000124: Nov 10 20:54:09.659: ISAKMP:(2001): vendor ID seems Unity/DPD but major 160 mismatch
000125: Nov 10 20:54:09.659: ISAKMP:(2001): vendor ID is XAUTH
000126: Nov 10 20:54:09.659: ISAKMP:received payload type 20
000127: Nov 10 20:54:09.659: ISAKMP (2001): His hash no match - this node outside NAT
000128: Nov 10 20:54:09.659: ISAKMP:received payload type 20
000129: Nov 10 20:54:09.659: ISAKMP (2001): No NAT Found for self or peer
000130: Nov 10 20:54:09.659: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
000131: Nov 10 20:54:09.659: ISAKMP:(2001):Old State = IKE_R_MM3 New State = IKE_R_MM3
000132: Nov 10 20:54:09.659: ISAKMP:(2001): sending packet to 11.11.11.11 my_port 500 peer_port 500 (R) MM_KEY_EXCH
000133: Nov 10 20:54:09.659: ISAKMP:(2001):Sending an IKE IPv4 Packet.
000134: Nov 10 20:54:09.659: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
000135: Nov 10 20:54:09.659: ISAKMP:(2001):Old State = IKE_R_MM3 New State = IKE_R_MM4
000136: Nov 10 20:54:09.667: ISAKMP (2001): received packet from 11.11.11.11 dport 500 sport 500 Global (R) MM_KEY_EXCH
000137: Nov 10 20:54:09.667: ISAKMP:(2001):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
000138: Nov 10 20:54:09.667: ISAKMP:(2001):Old State = IKE_R_MM4 New State = IKE_R_MM5
000139: Nov 10 20:54:09.667: ISAKMP:(2001): processing ID payload. message ID = 0
000140: Nov 10 20:54:09.667: ISAKMP (2001): ID payload
next-payload : 8
type : 1
address : 11.11.11.11
protocol : 17
port : 500
length : 12
000141: Nov 10 20:54:09.667: ISAKMP:(0):: peer matches *none* of the profiles
000142: Nov 10 20:54:09.667: ISAKMP:(2001): processing HASH payload. message ID = 0
000143: Nov 10 20:54:09.667: ISAKMP:received payload type 17
000144: Nov 10 20:54:09.667: ISAKMP:(2001): processing NOTIFY INITIAL_CONTACT protocol 1
spi 0, message ID = 0, sa = 0x1046561C
000145: Nov 10 20:54:09.667: ISAKMP:(2001):SA authentication status:
authenticated
000146: Nov 10 20:54:09.667: ISAKMP:(2001):SA has been authenticated with 11.11.11.11
000147: Nov 10 20:54:09.667: ISAKMP:(2001):SA authentication status:
authenticated
000148: Nov 10 20:54:09.667: ISAKMP:(2001): Process initial contact,
bring down existing phase 1 and 2 SA's with local 22.22.22.22 remote 11.11.11.11 remote port 500
000149: Nov 10 20:54:09.667: ISAKMP: Trying to insert a peer 22.22.22.22/11.11.11.11/500/, and inserted successfully 3410964.
000150: Nov 10 20:54:09.667: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
000151: Nov 10 20:54:09.667: ISAKMP:(2001):Old State = IKE_R_MM5 New State = IKE_R_MM5
000152: Nov 10 20:54:09.667: IPSEC(key_engine): got a queue event with 1 KMI message(s)
000153: Nov 10 20:54:09.667: ISAKMP:(2001):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
000154: Nov 10 20:54:09.667: ISAKMP (2001): ID payload
next-payload : 8
type : 1
address : 22.22.22.22
protocol : 17
port : 500
length : 12
000155: Nov 10 20:54:09.667: ISAKMP:(2001):Total payload length: 12
000156: Nov 10 20:54:09.667: ISAKMP:(2001): sending packet to 11.11.11.11 my_port 500 peer_port 500 (R) MM_KEY_EXCH
000157: Nov 10 20:54:09.667: ISAKMP:(2001):Sending an IKE IPv4 Packet.
000158: Nov 10 20:54:09.667: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
000159: Nov 10 20:54:09.667: ISAKMP:(2001):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
000160: Nov 10 20:54:09.667: ISAKMP:(2001):IKE_DPD is enabled, initializing timers
000161: Nov 10 20:54:09.667: ISAKMP:(2001):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
000162: Nov 10 20:54:09.667: ISAKMP:(2001):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
000163: Nov 10 20:54:09.671: ISAKMP (2001): received packet from 11.11.11.11 dport 500 sport 500 Global (R) QM_IDLE
000164: Nov 10 20:54:09.671: ISAKMP: set new node 2126720465 to QM_IDLE
000165: Nov 10 20:54:09.671: ISAKMP:(2001): processing HASH payload. message ID = 2126720465
000166: Nov 10 20:54:09.671: ISAKMP:(2001): processing SA payload. message ID = 2126720465
000167: Nov 10 20:54:09.671: ISAKMP:(2001):Checking IPSec proposal 1
000168: Nov 10 20:54:09.671: ISAKMP: transform 1, ESP_AES
000169: Nov 10 20:54:09.671: ISAKMP: attributes in transform:
000170: Nov 10 20:54:09.671: ISAKMP: encaps is 1 (Tunnel)
000171: Nov 10 20:54:09.671: ISAKMP: SA life type in seconds
000172: Nov 10 20:54:09.671: ISAKMP: SA life duration (basic) of 1200
000173: Nov 10 20:54:09.671: ISAKMP: SA life type in kilobytes
000174: Nov 10 20:54:09.671: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
000175: Nov 10 20:54:09.671: ISAKMP: authenticator is HMAC-SHA256
000176: Nov 10 20:54:09.671: ISAKMP: key length is 128
000177: Nov 10 20:54:09.671: ISAKMP: group is 14
000178: Nov 10 20:54:09.671: ISAKMP:(2001):atts are acceptable.
000179: Nov 10 20:54:09.671: IPSEC(validate_proposal_request): proposal part #1
000180: Nov 10 20:54:09.671: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 10.2.1.0/255.255.255.0/256/0,
remote_proxy= 10.1.1.0/255.255.255.0/256/0,
protocol= ESP, transform= NONE (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
000181: Nov 10 20:54:09.671: Crypto mapdb : proxy_match
src addr : 10.2.1.0
dst addr : 10.1.1.0
protocol : 0
src port : 0
dst port : 0
000182: Nov 10 20:54:09.671: (ipsec_process_proposal)Map Accepted: MAP-name, 160
000183: Nov 10 20:54:09.675: ISAKMP:(2001): processing NONCE payload. message ID = 2126720465
000184: Nov 10 20:54:09.675: ISAKMP:(2001): processing KE payload. message ID = 2126720465
000185: Nov 10 20:54:09.687: ISAKMP:(2001): processing ID payload. message ID = 2126720465
000186: Nov 10 20:54:09.687: ISAKMP:(2001): processing ID payload. message ID = 2126720465
000187: Nov 10 20:54:09.687: ISAKMP:(2001):QM Responder gets spi
000188: Nov 10 20:54:09.687: ISAKMP:(2001):Node 2126720465, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
000189: Nov 10 20:54:09.687: ISAKMP:(2001):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
000190: Nov 10 20:54:09.687: ISAKMP:(2001):Node 2126720465, Input = IKE_MESG_INTERNAL, IKE_GOT_SPI
000191: Nov 10 20:54:09.687: ISAKMP:(2001):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_IPSEC_INSTALL_AWAIT
000192: Nov 10 20:54:09.687: IPSEC(key_engine): got a queue event with 1 KMI message(s)
000193: Nov 10 20:54:09.687: Crypto mapdb : proxy_match
src addr : 10.2.1.0
dst addr : 10.1.1.0
protocol : 256
src port : 0
dst port : 0
000194: Nov 10 20:54:09.687: IPSEC(crypto_ipsec_create_ipsec_sas): Map found MAP-name, 160
000195: Nov 10 20:54:09.687: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and peer 11.11.11.11
000196: Nov 10 20:54:09.687: IPSEC(create_sa): sa created,
(sa) sa_dest= 22.22.22.22, sa_proto= 50,
sa_spi= 0xAC6FE00C(2893013004),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 1
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 10.2.1.0/255.255.255.0/256/0,
remote_proxy= 10.1.1.0/255.255.255.0/256/0
000197: Nov 10 20:54:09.687: IPSEC(create_sa): sa created,
(sa) sa_dest= 11.11.11.11, sa_proto= 50,
sa_spi= 0x3C27C1A1(1009238433),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 2
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 10.2.1.0/255.255.255.0/256/0,
remote_proxy= 10.1.1.0/255.255.255.0/256/0
000198: Nov 10 20:54:09.687: ISAKMP: Failed to find peer index node to update peer_info_list
000199: Nov 10 20:54:09.687: ISAKMP:(2001):Received IPSec Install callback... proceeding with the negotiation
000200: Nov 10 20:54:09.687: ISAKMP:(2001):Successfully installed IPSEC SA (SPI:0xAC6FE00C) on Dialer1
000201: Nov 10 20:54:09.687: ISAKMP:(2001): sending packet to 11.11.11.11 my_port 500 peer_port 500 (R) QM_IDLE
000202: Nov 10 20:54:09.687: ISAKMP:(2001):Sending an IKE IPv4 Packet.
000203: Nov 10 20:54:09.687: ISAKMP:(2001):Node 2126720465, Input = IKE_MESG_FROM_IPSEC, IPSEC_INSTALL_DONE
000204: Nov 10 20:54:09.687: ISAKMP:(2001):Old State = IKE_QM_IPSEC_INSTALL_AWAIT New State = IKE_QM_R_QM2
000205: Nov 10 20:54:09.707: ISAKMP (2001): received packet from 11.11.11.11 dport 500 sport 500 Global (R) QM_IDLE
000206: Nov 10 20:54:09.707: ISAKMP:(2001):deleting node 2126720465 error FALSE reason "QM done (await)"
000207: Nov 10 20:54:09.707: ISAKMP:(2001):Node 2126720465, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
000208: Nov 10 20:54:09.707: ISAKMP:(2001):Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE
000209: Nov 10 20:54:09.707: IPSEC(key_engine): got a queue event with 1 KMI message(s)
000210: Nov 10 20:54:09.707: IPSEC(key_engine_enable_outbound): rec'd enable notify from ISAKMP
000211: Nov 10 20:54:09.707: IPSEC: Expand action denied, notify RP
RT-2#
RT-2#no debug all
All possible debugging has been turned off
RT-2#
