Cisco
L2TPv2/IPsecのコンフィグ
ここではルータ間でIPsecをせず、拠点1のPCからRT-2にL2TPv2/IPsecする場合のコンフィグを記載します。
構成図
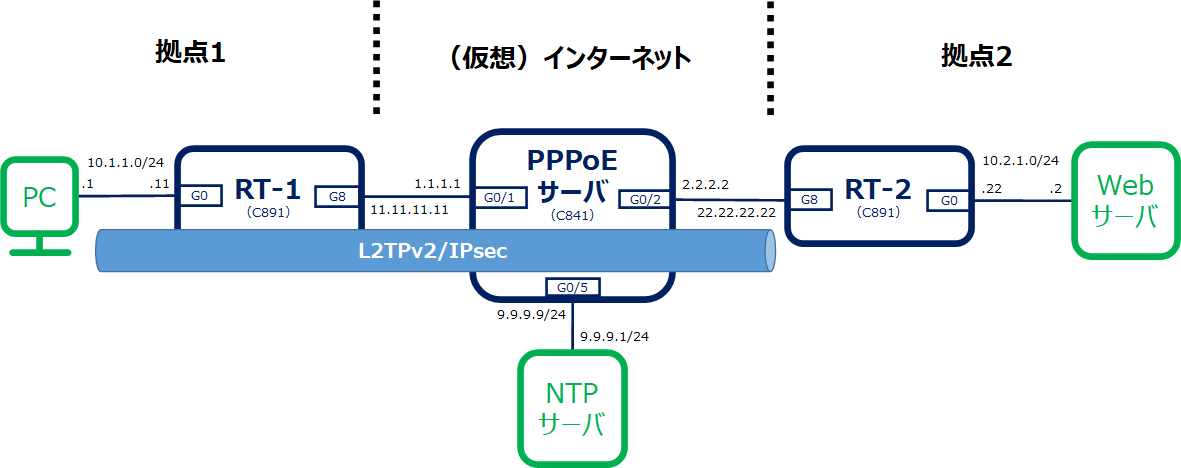
L2TPv2/IPsec接続時のイメージ図
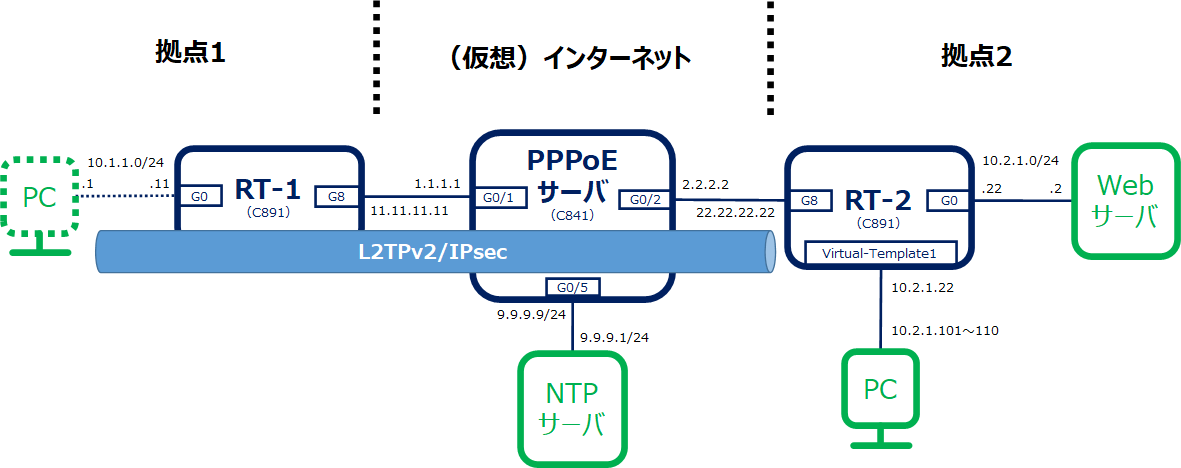
コンフィグについて
PC(L2TPアクセスコンセントレータ)はWindows10ビルトインソフトウェアを使用します。そのため、RT-2(L2TPネットワークサーバ)ではWindows10が対応している暗号/認証アルゴリズム、DHグループを設定します。
IPsecのオプション設定のISAKMPライフタイムの短縮とDPDの定期実行は設定しますが、PFSの有効化とIPsecライフタイムの短縮は設定しません。ネゴシエーションできなくなります。
NAPT越えするためNATトラバーサルが動作します。RT-2でUDP500(isakmp)だけでなく、UDP4500(non500-isakmp)からのアクセスも許可する必要があります。
RT-1コンフィグ
RT-2コンフィグ
※黄色文字はPPPoE+NAT+ACLのコンフィグからの変更箇所です。
RT-1#sh run
version 15.3
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime
service timestamps log datetime msec localtime
no service password-encryption
service sequence-numbers
no service dhcp
!
hostname RT-1
!
boot-start-marker
boot-end-marker
!
aqm-register-fnf
!
logging buffered 512000
enable secret 5 $1$UZ.d$263eCd7jDVJHAqwgfcFNL0
!
no aaa new-model
clock timezone JST 9 0
!
!
!
no ip bootp server
no ip domain lookup
ip domain name free-ne.com
ip inspect name CBAC tcp
ip inspect name CBAC udp
ip inspect name CBAC icmp
ip cef
no ipv6 cef
!
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
no spanning-tree vlan 1
username admin secret 5 $1$ztjJ$yET4V3rcbtkvdA9yjTJin.
!
!
!
ip ssh version 2
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface BRI0
no ip address
encapsulation hdlc
shutdown
isdn termination multidrop
!
interface FastEthernet0
no ip address
shutdown
duplex auto
speed auto
!
interface GigabitEthernet0
no ip address
!
interface GigabitEthernet1
no ip address
!
interface GigabitEthernet2
no ip address
!
interface GigabitEthernet3
no ip address
!
interface GigabitEthernet4
no ip address
!
interface GigabitEthernet5
no ip address
!
interface GigabitEthernet6
no ip address
!
interface GigabitEthernet7
no ip address
!
interface GigabitEthernet8
no ip address
duplex auto
speed auto
pppoe enable group global
pppoe-client dial-pool-number 1
!
!
!
!
!
!
!
!
!
interface Vlan1
ip address 10.1.1.11 255.255.255.0
ip nat inside
ip virtual-reassembly in
ip tcp adjust-mss 1350
!
interface Async3
no ip address
encapsulation slip
!
interface Dialer1
ip address negotiated
ip access-group Internet-ACL in
ip mtu 1492
ip nat outside
ip inspect CBAC out
ip virtual-reassembly in
encapsulation ppp
dialer pool 1
dialer-group 10
ppp authentication chap callin
ppp chap hostname user1
ppp chap password 0 cisco
no cdp enable
!
!
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
!
ip nat inside source list Internet-PAT interface Dialer1 overload
!
ip route 0.0.0.0 0.0.0.0 Dialer1
!
ip access-list standard Internet-PAT
permit 10.1.1.0 0.0.0.255
ip access-list standard SSH-ACL
permit 10.1.1.0 0.0.0.255
!
ip access-list extended Internet-ACL
permit udp host 9.9.9.1 eq ntp host 11.11.11.11 eq ntp
permit icmp any host 11.11.11.11
!
!
!
!
!
dialer-list 10 protocol ip permit
no cdp run
!
!
control-plane
!
!
!
mgcp behavior rsip-range tgcp-only
mgcp behavior comedia-role none
mgcp behavior comedia-check-media-src disable
mgcp behavior comedia-sdp-force disable
!
mgcp profile default
!
!
!
line con 0
exec-timeout 60 0
logging synchronous
no modem enable
line aux 0
line 3
modem InOut
speed 115200
flowcontrol hardware
line vty 0 4
access-class SSH-ACL in
exec-timeout 60 0
logging synchronous
login local
transport input ssh
!
scheduler allocate 20000 1000
ntp server 9.9.9.1
!
end
RT-2#show run version 15.3 no service pad service tcp-keepalives-in service tcp-keepalives-out service timestamps debug datetime msec localtime service timestamps log datetime msec localtime no service password-encryption service sequence-numbers no service dhcp ! hostname RT-2 ! boot-start-marker boot-end-marker ! aqm-register-fnf ! logging buffered 512000 enable secret 5 $1$RBil$/zAAQLKQrekcrMgQIHCwW1 ! no aaa new-model clock timezone JST 9 0 ! ! ! no ip bootp server no ip domain lookup ip domain name free-ne.com ip inspect name CBAC tcp ip inspect name CBAC udp ip inspect name CBAC icmp ip cef no ipv6 cef ! ! ! multilink bundle-name authenticated vpdn enable ! vpdn-group VPDN-name ! Default L2TP VPDN group accept-dialin protocol l2tp virtual-template 1 no l2tp tunnel authentication ! ! ! no spanning-tree vlan 1 username admin password 0 cisco ! ! ! ip ssh version 2 ! ! crypto isakmp policy 110 encr aes authentication pre-share group 19 lifetime 1800 crypto isakmp key PS-key address 0.0.0.0 crypto isakmp keepalive 30 periodic ! ! crypto ipsec transform-set TS-name esp-aes esp-sha-hmac mode transport ! ! ! crypto dynamic-map DMAP-name 10 set nat demux set transform-set TS-name ! ! crypto map MAP-name 1000 ipsec-isakmp dynamic DMAP-name ! ! ! interface BRI0 no ip address encapsulation hdlc shutdown isdn termination multidrop ! interface FastEthernet0 no ip address shutdown duplex auto speed auto ! interface GigabitEthernet0 no ip address ! interface GigabitEthernet1 no ip address ! interface GigabitEthernet2 no ip address ! interface GigabitEthernet3 no ip address ! interface GigabitEthernet4 no ip address ! interface GigabitEthernet5 no ip address ! interface GigabitEthernet6 no ip address ! interface GigabitEthernet7 no ip address ! interface GigabitEthernet8 no ip address duplex auto speed auto pppoe enable group global pppoe-client dial-pool-number 1 ! interface Virtual-Template1 ip unnumbered Vlan1 ip nat inside ip virtual-reassembly in ip tcp adjust-mss 1350 peer default ip address pool Pool-name ppp authentication chap ms-chap-v2 ! interface Vlan1 ip address 10.2.1.22 255.255.255.0 ip nat inside ip virtual-reassembly in ip tcp adjust-mss 1452 ! interface Async3 no ip address encapsulation slip ! interface Dialer1 ip address negotiated ip access-group Internet-ACL in ip mtu 1492 ip nat outside ip inspect CBAC out ip virtual-reassembly in encapsulation ppp dialer pool 1 dialer-group 10 ppp authentication chap callin ppp chap hostname user1 ppp chap password 0 cisco no cdp enable crypto map MAP-name ! ip local pool Pool-name 10.2.1.101 10.2.1.110 ip forward-protocol nd no ip http server no ip http secure-server ! ! ip nat inside source list Internet-PAT interface Dialer1 overload ip nat inside source static tcp 10.2.1.2 80 22.22.22.22 80 extendable ip route 0.0.0.0 0.0.0.0 Dialer1 ! ip access-list standard Internet-PAT permit 10.2.1.0 0.0.0.255 ip access-list standard SSH-ACL permit 10.2.1.0 0.0.0.255 ! ip access-list extended Internet-ACL permit udp host 9.9.9.1 eq ntp host 22.22.22.22 eq ntp permit icmp any host 22.22.22.22 permit tcp any host 22.22.22.22 eq www permit udp host 11.11.11.11 eq isakmp host 22.22.22.22 eq isakmp permit udp host 11.11.11.11 eq non500-isakmp host 22.22.22.22 eq non500-isakmp permit esp host 11.11.11.11 host 22.22.22.22 ! dialer-list 10 protocol ip permit no cdp run ! ! control-plane ! ! ! mgcp behavior rsip-range tgcp-only mgcp behavior comedia-role none mgcp behavior comedia-check-media-src disable mgcp behavior comedia-sdp-force disable ! mgcp profile default ! ! ! line con 0 exec-timeout 60 0 logging synchronous no modem enable line aux 0 line 3 modem InOut speed 115200 flowcontrol hardware line vty 0 4 access-class SSH-ACL in exec-timeout 60 0 logging synchronous login local transport input ssh ! scheduler allocate 20000 1000 ntp server 9.9.9.1 ! end
IPsecの状態確認
RT-2#show crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec AES+SHA 0 137 137 22.22.22.22
2 IPsec AES+SHA 79 0 0 22.22.22.22
2001 IKE SHA+AES 0 0 0 22.22.22.22
RT-2#
RT-2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
22.22.22.22 11.11.11.11 QM_IDLE 2001 ACTIVE
IPv6 Crypto ISAKMP SA
RT-2#
RT-2#show crypto ipsec sa
interface: Dialer1
Crypto map tag: MAP-name, local addr 22.22.22.22
protected vrf: (none)
local ident (addr/mask/prot/port): (22.22.22.22/255.255.255.255/17/1701)
remote ident (addr/mask/prot/port): (11.11.11.11/255.255.255.255/17/4500)
current_peer 11.11.11.11 port 4500
PERMIT, flags={}
#pkts encaps: 84, #pkts encrypt: 84, #pkts digest: 84
#pkts decaps: 142, #pkts decrypt: 142, #pkts verify: 142
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 22.22.22.22, remote crypto endpt.: 11.11.11.11
plaintext mtu 1442, path mtu 1492, ip mtu 1492, ip mtu idb Dialer1
current outbound spi: 0x745599E2(1951767010)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x2F5BBFC8(794542024)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport UDP-Encaps, }
conn id: 1, flow_id: Onboard VPN:1, sibling_flags 80000000, crypto map: MAP-name
sa timing: remaining key lifetime (k/sec): (227029/3288)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x745599E2(1951767010)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport UDP-Encaps, }
conn id: 2, flow_id: Onboard VPN:2, sibling_flags 80000000, crypto map: MAP-name
sa timing: remaining key lifetime (k/sec): (227041/3288)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
RT-2#
MSS
MSSは余裕を持たせた値にしています。
ちなみに、この環境でのMSSの最大値は以下です。
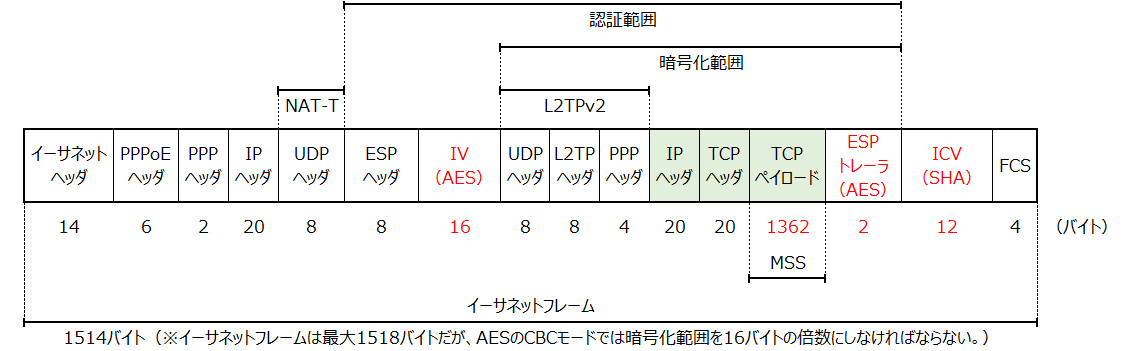
ヘッダについてはMTU/MSS確認用フレームフォーマット図に記載しています。
Windows10対応の暗号/認証アルゴリズム
Windows10が対応している暗号/認証アルゴリズム、DHグループをRT-2のデバッグログで確認しました。
フェーズ1
000525: *Mar 12 11:15:24.651: ISAKMP:(0):Checking ISAKMP transform 1 against priority 110 policy 000526: *Mar 12 11:15:24.651: ISAKMP: encryption AES-CBC 000527: *Mar 12 11:15:24.651: ISAKMP: keylength of 256 000528: *Mar 12 11:15:24.651: ISAKMP: hash SHA 000529: *Mar 12 11:15:24.651: ISAKMP: default group 20 000530: *Mar 12 11:15:24.651: ISAKMP: auth pre-share 000531: *Mar 12 11:15:24.651: ISAKMP: life type in seconds 000532: *Mar 12 11:15:24.651: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80 000533: *Mar 12 11:15:24.651: ISAKMP:(0):Hash algorithm offered does not match policy! 000534: *Mar 12 11:15:24.651: ISAKMP:(0):atts are not acceptable. Next payload is 3 000535: *Mar 12 11:15:24.651: ISAKMP:(0):Checking ISAKMP transform 2 against priority 110 policy 000536: *Mar 12 11:15:24.651: ISAKMP: encryption AES-CBC 000537: *Mar 12 11:15:24.651: ISAKMP: keylength of 128 000538: *Mar 12 11:15:24.651: ISAKMP: hash SHA 000539: *Mar 12 11:15:24.651: ISAKMP: default group 19 000540: *Mar 12 11:15:24.651: ISAKMP: auth pre-share 000541: *Mar 12 11:15:24.651: ISAKMP: life type in seconds 000542: *Mar 12 11:15:24.651: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80 000543: *Mar 12 11:15:24.651: ISAKMP:(0):Hash algorithm offered does not match policy! 000544: *Mar 12 11:15:24.651: ISAKMP:(0):atts are not acceptable. Next payload is 3 000545: *Mar 12 11:15:24.651: ISAKMP:(0):Checking ISAKMP transform 3 against priority 110 policy 000546: *Mar 12 11:15:24.651: ISAKMP: encryption AES-CBC 000547: *Mar 12 11:15:24.651: ISAKMP: keylength of 256 000548: *Mar 12 11:15:24.651: ISAKMP: hash SHA 000549: *Mar 12 11:15:24.651: ISAKMP: default group 14 000550: *Mar 12 11:15:24.651: ISAKMP: auth pre-share 000551: *Mar 12 11:15:24.651: ISAKMP: life type in seconds 000552: *Mar 12 11:15:24.651: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80 000553: *Mar 12 11:15:24.655: ISAKMP:(0):Hash algorithm offered does not match policy! 000554: *Mar 12 11:15:24.655: ISAKMP:(0):atts are not acceptable. Next payload is 3 000555: *Mar 12 11:15:24.655: ISAKMP:(0):Checking ISAKMP transform 4 against priority 110 policy 000556: *Mar 12 11:15:24.655: ISAKMP: encryption 3DES-CBC 000557: *Mar 12 11:15:24.655: ISAKMP: hash SHA 000558: *Mar 12 11:15:24.655: ISAKMP: default group 14 000559: *Mar 12 11:15:24.655: ISAKMP: auth pre-share 000560: *Mar 12 11:15:24.655: ISAKMP: life type in seconds 000561: *Mar 12 11:15:24.655: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80 000562: *Mar 12 11:15:24.655: ISAKMP:(0):Encryption algorithm offered does not match policy! 000563: *Mar 12 11:15:24.655: ISAKMP:(0):atts are not acceptable. Next payload is 3 000564: *Mar 12 11:15:24.655: ISAKMP:(0):Checking ISAKMP transform 5 against priority 110 policy 000565: *Mar 12 11:15:24.655: ISAKMP: encryption 3DES-CBC 000566: *Mar 12 11:15:24.655: ISAKMP: hash SHA 000567: *Mar 12 11:15:24.655: ISAKMP: default group 2 000568: *Mar 12 11:15:24.655: ISAKMP: auth pre-share 000569: *Mar 12 11:15:24.655: ISAKMP: life type in seconds 000570: *Mar 12 11:15:24.655: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80 000571: *Mar 12 11:15:24.655: ISAKMP:(0):Encryption algorithm offered does not match policy!
フェーズ2
000384: *Mar 12 11:12:45.299: ISAKMP:(2002):Checking IPSec proposal 1
000385: *Mar 12 11:12:45.299: ISAKMP: transform 1, ESP_AES
000386: *Mar 12 11:12:45.299: ISAKMP: attributes in transform:
000387: *Mar 12 11:12:45.299: ISAKMP: encaps is 4 (Transport-UDP)
000388: *Mar 12 11:12:45.299: ISAKMP: key length is 256
000389: *Mar 12 11:12:45.299: ISAKMP: authenticator is HMAC-SHA
000390: *Mar 12 11:12:45.299: ISAKMP: SA life type in seconds
000391: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
000392: *Mar 12 11:12:45.299: ISAKMP: SA life type in kilobytes
000393: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x3 0xD0 0x90
000394: *Mar 12 11:12:45.299: ISAKMP:(2002):atts are acceptable.
000395: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1
000396: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 22.22.22.22/255.255.255.255/17/1701,
remote_proxy= 11.11.11.11/255.255.255.255/17/1701,
protocol= ESP, transform= NONE (Transport-UDP),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
000397: *Mar 12 11:12:45.299: Cannot find crypto swsb : in ipsec_process_proposal (), 1590
000398: *Mar 12 11:12:45.299: IPSEC(ipsec_process_proposal): transform proposal not supported for identity:
{esp-aes 256 esp-sha-hmac }
000399: *Mar 12 11:12:45.299: ISAKMP:(2002): IPSec policy invalidated proposal with error 256
000400: *Mar 12 11:12:45.299: ISAKMP:(2002):Checking IPSec proposal 2
000401: *Mar 12 11:12:45.299: ISAKMP: transform 1, ESP_AES
000402: *Mar 12 11:12:45.299: ISAKMP: attributes in transform:
000403: *Mar 12 11:12:45.299: ISAKMP: encaps is 4 (Transport-UDP)
000404: *Mar 12 11:12:45.299: ISAKMP: key length is 128
000405: *Mar 12 11:12:45.299: ISAKMP: authenticator is HMAC-SHA
000406: *Mar 12 11:12:45.299: ISAKMP: SA life type in seconds
000407: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
000408: *Mar 12 11:12:45.299: ISAKMP: SA life type in kilobytes
000409: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x3 0xD0 0x90
000410: *Mar 12 11:12:45.299: ISAKMP:(2002):atts are acceptable.
000411: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1
000412: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 22.22.22.22/255.255.255.255/17/1701,
remote_proxy= 11.11.11.11/255.255.255.255/17/1701,
protocol= ESP, transform= NONE (Transport-UDP),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
000413: *Mar 12 11:12:45.299: Cannot find crypto swsb : in ipsec_process_proposal (), 1590
000414: *Mar 12 11:12:45.299: IPSEC(ipsec_process_proposal): transform proposal not supported for identity:
{esp-aes esp-sha-hmac }
000415: *Mar 12 11:12:45.299: ISAKMP:(2002): IPSec policy invalidated proposal with error 256
000416: *Mar 12 11:12:45.299: ISAKMP:(2002):Checking IPSec proposal 3
000417: *Mar 12 11:12:45.299: ISAKMP: transform 1, ESP_3DES
000418: *Mar 12 11:12:45.299: ISAKMP: attributes in transform:
000419: *Mar 12 11:12:45.299: ISAKMP: encaps is 4 (Transport-UDP)
000420: *Mar 12 11:12:45.299: ISAKMP: authenticator is HMAC-SHA
000421: *Mar 12 11:12:45.299: ISAKMP: SA life type in seconds
000422: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
000423: *Mar 12 11:12:45.299: ISAKMP: SA life type in kilobytes
000424: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x3 0xD0 0x90
000425: *Mar 12 11:12:45.299: ISAKMP:(2002):atts are acceptable.
000426: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1
000427: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 22.22.22.22/255.255.255.255/17/1701,
remote_proxy= 11.11.11.11/255.255.255.255/17/1701,
protocol= ESP, transform= NONE (Transport-UDP),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
000428: *Mar 12 11:12:45.299: Cannot find crypto swsb : in ipsec_process_proposal (), 1590
000429: *Mar 12 11:12:45.299: IPSEC(ipsec_process_proposal): transform proposal not supported for identity:
{esp-3des esp-sha-hmac }
000430: *Mar 12 11:12:45.299: ISAKMP:(2002): IPSec policy invalidated proposal with error 256
000431: *Mar 12 11:12:45.299: ISAKMP:(2002):Checking IPSec proposal 4
000432: *Mar 12 11:12:45.299: ISAKMP: transform 1, ESP_DES
000433: *Mar 12 11:12:45.299: ISAKMP: attributes in transform:
000434: *Mar 12 11:12:45.299: ISAKMP: encaps is 4 (Transport-UDP)
000435: *Mar 12 11:12:45.299: ISAKMP: authenticator is HMAC-SHA
000436: *Mar 12 11:12:45.299: ISAKMP: SA life type in seconds
000437: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
000438: *Mar 12 11:12:45.299: ISAKMP: SA life type in kilobytes
000439: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x3 0xD0 0x90
000440: *Mar 12 11:12:45.299: ISAKMP:(2002):atts are acceptable.
000441: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1
000442: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 22.22.22.22/255.255.255.255/17/1701,
remote_proxy= 11.11.11.11/255.255.255.255/17/1701,
protocol= ESP, transform= NONE (Transport-UDP),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
000443: *Mar 12 11:12:45.299: Cannot find crypto swsb : in ipsec_process_proposal (), 1590
000444: *Mar 12 11:12:45.299: IPSEC(ipsec_process_proposal): transform proposal not supported for identity:
{esp-des esp-sha-hmac }
000445: *Mar 12 11:12:45.299: ISAKMP:(2002): IPSec policy invalidated proposal with error 256
000446: *Mar 12 11:12:45.299: ISAKMP:(2002):Checking IPSec proposal 5
000447: *Mar 12 11:12:45.299: ISAKMP: transform 1, ESP_NULL
000448: *Mar 12 11:12:45.299: ISAKMP: attributes in transform:
000449: *Mar 12 11:12:45.299: ISAKMP: encaps is 4 (Transport-UDP)
000450: *Mar 12 11:12:45.299: ISAKMP: authenticator is HMAC-SHA
000451: *Mar 12 11:12:45.299: ISAKMP: SA life type in seconds
000452: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
000453: *Mar 12 11:12:45.299: ISAKMP: SA life type in kilobytes
000454: *Mar 12 11:12:45.299: ISAKMP: SA life duration (VPI) of 0x0 0x3 0xD0 0x90
000455: *Mar 12 11:12:45.299: ISAKMP:(2002):atts are acceptable.
000456: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1
000457: *Mar 12 11:12:45.299: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 22.22.22.22/255.255.255.255/17/1701,
remote_proxy= 11.11.11.11/255.255.255.255/17/1701,
protocol= ESP, transform= NONE (Transport-UDP),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
000458: *Mar 12 11:12:45.299: Cannot find crypto swsb : in ipsec_process_proposal (), 1590
000459: *Mar 12 11:12:45.299: IPSEC(ipsec_process_proposal): transform proposal not supported for identity:
{esp-null esp-sha-hmac }
