SRX
IPsec+PPPoE+DstNAT+Filterのコンフィグ
IPsec+PPPoE+NAT+ACLのコンフィグでは、Ciscoルータ同士でIPsecをしていますが、ここではRT-2をSRX100に置き換え、CiscoルータとSRXでIPsecをする場合のコンフィグを記載します。
構成図
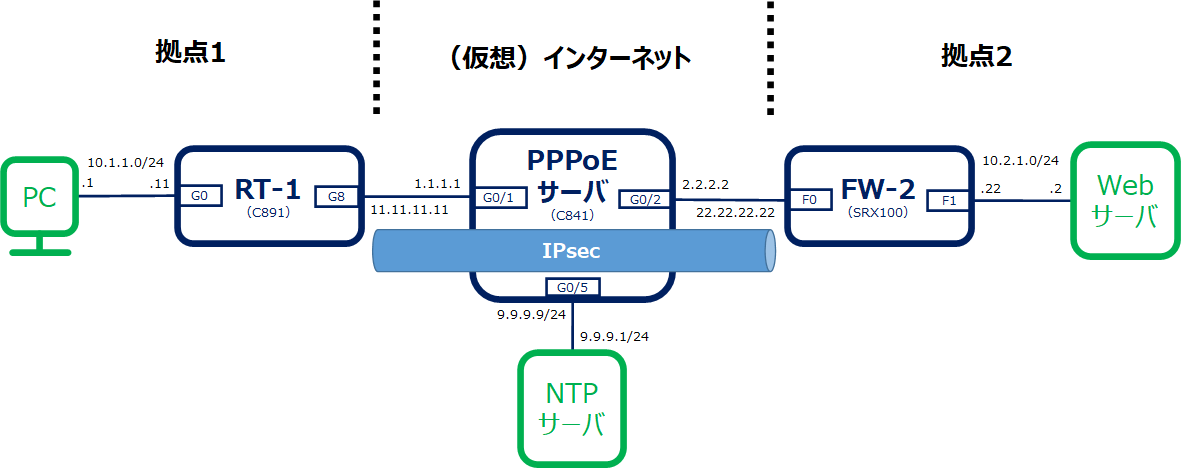
コンフィグについて
RT-1のコンフィグはIPsec+PPPoE+NAT+ACLのコンフィグと同じです。
FW-2にはプロキシIDを設定しています。他メーカー機器同士のIPsecで、フェーズ1まで成功し、フェーズ2が失敗しているとき、このプロキシIDのズレが原因となっている場合が多いです。
FW-2コンフィグ
※黄色文字はPPPoE+DstNAT+Filterのコンフィグからの変更箇所です。
root@FW-2> show configuration | display set | no-more set version 12.1X46-D35.1 set system host-name FW-2 set system time-zone Asia/Tokyo set system root-authentication encrypted-password "$1$v9DrLuxC$5NOkmRqvMmEHBCqO9Ws0q." set system services ssh set system services web-management https system-generated-certificate set system services dhcp propagate-ppp-settings pp0.0 set system syslog archive size 100k set system syslog archive files 3 set system syslog user * any emergency set system syslog file messages any critical set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands error set system max-configurations-on-flash 5 set system max-configuration-rollbacks 5 set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set system ntp server 9.9.9.1 set interfaces fe-0/0/0 fastether-options no-auto-negotiation set interfaces fe-0/0/0 unit 0 encapsulation ppp-over-ether set interfaces fe-0/0/1 unit 0 family ethernet-switching set interfaces fe-0/0/2 unit 0 family ethernet-switching set interfaces fe-0/0/3 unit 0 family ethernet-switching set interfaces fe-0/0/4 unit 0 family ethernet-switching set interfaces fe-0/0/5 unit 0 family ethernet-switching set interfaces fe-0/0/6 unit 0 family ethernet-switching set interfaces fe-0/0/7 unit 0 family ethernet-switching set interfaces lo0 unit 0 family inet filter input Filter1 set interfaces pp0 unit 0 ppp-options chap default-chap-secret "$9$kPfzpu1hyK5Q1h" set interfaces pp0 unit 0 ppp-options chap local-name user1 set interfaces pp0 unit 0 ppp-options chap passive set interfaces pp0 unit 0 pppoe-options underlying-interface fe-0/0/0.0 set interfaces pp0 unit 0 family inet mtu 1492 set interfaces pp0 unit 0 family inet negotiate-address set interfaces st0 unit 0 family inet set interfaces vlan unit 0 family inet address 10.2.1.22/24 set routing-options static route 0.0.0.0/0 qualified-next-hop pp0.0 metric 1 set routing-options static route 10.1.1.0/24 next-hop st0.0 set security ike proposal IKE-Proposal authentication-method pre-shared-keys set security ike proposal IKE-Proposal dh-group group2 set security ike proposal IKE-Proposal authentication-algorithm sha-256 set security ike proposal IKE-Proposal encryption-algorithm aes-128-cbc set security ike proposal IKE-Proposal lifetime-seconds 1800 set security ike policy IKE-Policy mode main set security ike policy IKE-Policy proposals IKE-Proposal set security ike policy IKE-Policy pre-shared-key ascii-text "$9$q.TF/CpIEcQFCuOIle" set security ike gateway IKE-Gateway ike-policy IKE-Policy set security ike gateway IKE-Gateway address 11.11.11.11 set security ike gateway IKE-Gateway dead-peer-detection probe-idle-tunnel set security ike gateway IKE-Gateway dead-peer-detection interval 30 set security ike gateway IKE-Gateway external-interface pp0 set security ipsec proposal IPsec-Proposal protocol esp set security ipsec proposal IPsec-Proposal authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPsec-Proposal encryption-algorithm aes-128-cbc set security ipsec proposal IPsec-Proposal lifetime-seconds 1200 set security ipsec policy IPsec-Policy perfect-forward-secrecy keys group14 set security ipsec policy IPsec-Policy proposals IPsec-Proposal set security ipsec vpn IPsec-VPN bind-interface st0.0 set security ipsec vpn IPsec-VPN ike gateway IKE-Gateway set security ipsec vpn IPsec-VPN ike proxy-identity local 10.2.1.0/24 set security ipsec vpn IPsec-VPN ike proxy-identity remote 10.1.1.0/24 set security ipsec vpn IPsec-VPN ike proxy-identity service any set security ipsec vpn IPsec-VPN ike ipsec-policy IPsec-Policy set security flow tcp-mss all-tcp mss 1350 set security screen ids-option untrust-screen icmp ping-death set security screen ids-option untrust-screen ip source-route-option set security screen ids-option untrust-screen ip tear-drop set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200 set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048 set security screen ids-option untrust-screen tcp syn-flood timeout 20 set security screen ids-option untrust-screen tcp land set security nat source rule-set trust-to-untrust from zone trust set security nat source rule-set trust-to-untrust to zone untrust set security nat source rule-set trust-to-untrust rule source-nat-rule match source-address 0.0.0.0/0 set security nat source rule-set trust-to-untrust rule source-nat-rule then source-nat interface set security nat destination pool DstPool-HTTP address 10.2.1.2/32 set security nat destination pool DstPool-HTTP address port 80 set security nat destination rule-set DstNAT-Untrust from zone untrust set security nat destination rule-set DstNAT-Untrust rule DstNAT-HTTP match destination-address 22.22.22.22/32 set security nat destination rule-set DstNAT-Untrust rule DstNAT-HTTP match destination-port 80 set security nat destination rule-set DstNAT-Untrust rule DstNAT-HTTP match protocol tcp set security nat destination rule-set DstNAT-Untrust rule DstNAT-HTTP then destination-nat pool DstPool-HTTP set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit set security policies from-zone untrust to-zone trust policy Policy-HTTP match source-address any set security policies from-zone untrust to-zone trust policy Policy-HTTP match destination-address 10.2.1.2/32 set security policies from-zone untrust to-zone trust policy Policy-HTTP match application junos-http set security policies from-zone untrust to-zone trust policy Policy-HTTP then permit set security policies from-zone trust to-zone IPsec policy IPsec-Out match source-address 10.2.1.0/24 set security policies from-zone trust to-zone IPsec policy IPsec-Out match destination-address 10.1.1.0/24 set security policies from-zone trust to-zone IPsec policy IPsec-Out match application any set security policies from-zone trust to-zone IPsec policy IPsec-Out then permit set security policies from-zone IPsec to-zone trust policy IPsec-In match source-address 10.1.1.0/24 set security policies from-zone IPsec to-zone trust policy IPsec-In match destination-address 10.2.1.0/24 set security policies from-zone IPsec to-zone trust policy IPsec-In match application any set security policies from-zone IPsec to-zone trust policy IPsec-In then permit set security zones security-zone trust address-book address 10.2.1.2/32 10.2.1.2/32 set security zones security-zone trust address-book address 10.2.1.0/24 10.2.1.0/24 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust interfaces vlan.0 set security zones security-zone untrust address-book address 11.11.11.11/32 11.11.11.11/32 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust interfaces pp0.0 set security zones security-zone IPsec address-book address 10.1.1.0/24 10.1.1.0/24 set security zones security-zone IPsec host-inbound-traffic system-services all set security zones security-zone IPsec interfaces st0.0 set firewall family inet filter Filter1 term Term-ICMP from protocol icmp set firewall family inet filter Filter1 term Term-ICMP then accept set firewall family inet filter Filter1 term Term-MNG from source-address 10.2.1.0/24 set firewall family inet filter Filter1 term Term-MNG from source-address 10.1.1.0/24 set firewall family inet filter Filter1 term Term-MNG from protocol tcp set firewall family inet filter Filter1 term Term-MNG from destination-port ssh set firewall family inet filter Filter1 term Term-MNG from destination-port https set firewall family inet filter Filter1 term Term-MNG then log set firewall family inet filter Filter1 term Term-MNG then accept set firewall family inet filter Filter1 term Term-IPsec from source-address 11.11.11.11/32 set firewall family inet filter Filter1 term Term-IPsec from protocol udp set firewall family inet filter Filter1 term Term-IPsec from protocol esp set firewall family inet filter Filter1 term Term-IPsec from destination-port 500 set firewall family inet filter Filter1 term Term-IPsec then accept set vlans default l3-interface vlan.0 root@FW-2>
IPsecの状態確認
root@FW-2> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
1307827 UP 8f37ec83084eb267 687c1a222d5ff01b Main 11.11.11.11
root@FW-2> show security ike security-associations detail
IKE peer 11.11.11.11, Index 1307827, Gateway Name: IKE-Gateway
Role: Responder, State: UP
Initiator cookie: 8f37ec83084eb267, Responder cookie: 687c1a222d5ff01b
Exchange type: Main, Authentication method: Pre-shared-keys
Local: 22.22.22.22:500, Remote: 11.11.11.11:500
Lifetime: Expires in 610 seconds
Peer ike-id: 11.11.11.11
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes128-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-2
Traffic statistics:
Input bytes : 6020
Output bytes : 5968
Input packets: 47
Output packets: 48
Flags: IKE SA is created
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 0
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 22.22.22.22:500, Remote: 11.11.11.11:500
Local identity: 22.22.22.22
Remote identity: 11.11.11.11
Flags: IKE SA is created
root@FW-2> show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-cbc-128/sha256 84ece896 971/ 4608000 - root 500 11.11.11.11
>131073 ESP:aes-cbc-128/sha256 c9e0d0ad 971/ 4608000 - root 500 11.11.11.11
root@FW-2> show security ipsec security-associations detail
ID: 131073 Virtual-system: root, VPN Name: IPsec-VPN
Local Gateway: 22.22.22.22, Remote Gateway: 11.11.11.11
Local Identity: ipv4_subnet(any:0,[0..7]=10.2.1.0/24)
Remote Identity: ipv4_subnet(any:0,[0..7]=10.1.1.0/24)
Version: IKEv1
DF-bit: clear
Bind-interface: st0.0
Port: 500, Nego#: 7, Fail#: 0, Def-Del#: 0 Flag: 0x600a29
Last Tunnel Down Reason: Lifetime expired
Direction: inbound, SPI: 84ece896, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 964 seconds
Lifesize Remaining: 4608000 kilobytes
Soft lifetime: Expires in 700 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (128 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: c9e0d0ad, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 964 seconds
Lifesize Remaining: 4608000 kilobytes
Soft lifetime: Expires in 700 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (128 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
root@FW-2>
