SRX
PPPoE+DstNAT+Filterのコンフィグ
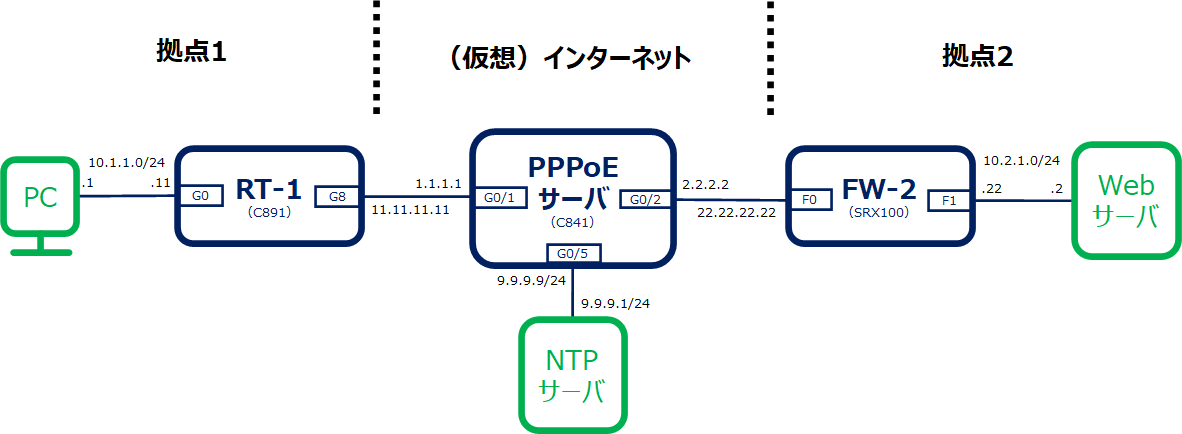
PPPoE+NAT+ACLのコンフィグでは、RT-1とRT-2はCiscoルータで構築していますが、ここではRT-2をSRX100に置き換えたコンフィグを記載します。SRX100のホスト名はFW-2とします。
構成図
コンフィグについて
RT-1のコンフィグはPPPoE+NAT+ACLのコンフィグと同じです。
FW-2への管理アクセスはSSHだけでなく、HTTPSもできるようにします。
FW-2コンフィグ
root@FW-2> show configuration | display set | no-more set version 12.1X46-D35.1 set system host-name FW-2 set system time-zone Asia/Tokyo set system root-authentication encrypted-password "$1$v9DrLuxC$5NOkmRqvMmEHBCqO9Ws0q." set system services ssh set system services web-management https system-generated-certificate set system services dhcp propagate-ppp-settings pp0.0 set system syslog archive size 100k set system syslog archive files 3 set system syslog user * any emergency set system syslog file messages any critical set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands error set system max-configurations-on-flash 5 set system max-configuration-rollbacks 5 set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set system ntp server 9.9.9.1 set interfaces fe-0/0/0 fastether-options no-auto-negotiation set interfaces fe-0/0/0 unit 0 encapsulation ppp-over-ether set interfaces fe-0/0/1 unit 0 family ethernet-switching set interfaces fe-0/0/2 unit 0 family ethernet-switching set interfaces fe-0/0/3 unit 0 family ethernet-switching set interfaces fe-0/0/4 unit 0 family ethernet-switching set interfaces fe-0/0/5 unit 0 family ethernet-switching set interfaces fe-0/0/6 unit 0 family ethernet-switching set interfaces fe-0/0/7 unit 0 family ethernet-switching set interfaces lo0 unit 0 family inet filter input Filter1 set interfaces pp0 unit 0 ppp-options chap default-chap-secret "$9$kPfzpu1hyK5Q1h" set interfaces pp0 unit 0 ppp-options chap local-name user1 set interfaces pp0 unit 0 ppp-options chap passive set interfaces pp0 unit 0 pppoe-options underlying-interface fe-0/0/0.0 set interfaces pp0 unit 0 family inet mtu 1492 set interfaces pp0 unit 0 family inet negotiate-address set interfaces vlan unit 0 family inet address 10.2.1.22/24 set routing-options static route 0.0.0.0/0 qualified-next-hop pp0.0 metric 1 set security flow tcp-mss all-tcp mss 1452 set security screen ids-option untrust-screen icmp ping-death set security screen ids-option untrust-screen ip source-route-option set security screen ids-option untrust-screen ip tear-drop set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200 set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024 set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048 set security screen ids-option untrust-screen tcp syn-flood timeout 20 set security screen ids-option untrust-screen tcp land set security nat source rule-set trust-to-untrust from zone trust set security nat source rule-set trust-to-untrust to zone untrust set security nat source rule-set trust-to-untrust rule source-nat-rule match source-address 0.0.0.0/0 set security nat source rule-set trust-to-untrust rule source-nat-rule then source-nat interface set security nat destination pool DstPool-SSH address 10.2.1.2/32 set security nat destination pool DstPool-SSH address port 22 set security nat destination pool DstPool-HTTP address 10.2.1.2/32 set security nat destination pool DstPool-HTTP address port 80 set security nat destination rule-set DstNAT-Untrust from zone untrust set security nat destination rule-set DstNAT-Untrust rule DstNAT-SSH match destination-address 22.22.22.22/32 set security nat destination rule-set DstNAT-Untrust rule DstNAT-SSH match destination-port 22222 set security nat destination rule-set DstNAT-Untrust rule DstNAT-SSH match protocol tcp set security nat destination rule-set DstNAT-Untrust rule DstNAT-SSH then destination-nat pool DstPool-SSH set security nat destination rule-set DstNAT-Untrust rule DstNAT-HTTP match destination-address 22.22.22.22/32 set security nat destination rule-set DstNAT-Untrust rule DstNAT-HTTP match destination-port 80 set security nat destination rule-set DstNAT-Untrust rule DstNAT-HTTP match protocol tcp set security nat destination rule-set DstNAT-Untrust rule DstNAT-HTTP then destination-nat pool DstPool-HTTP set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit set security policies from-zone untrust to-zone trust policy Policy-SSH match source-address 11.11.11.11/32 set security policies from-zone untrust to-zone trust policy Policy-SSH match destination-address 10.2.1.2/32 set security policies from-zone untrust to-zone trust policy Policy-SSH match application junos-ssh set security policies from-zone untrust to-zone trust policy Policy-SSH then permit set security policies from-zone untrust to-zone trust policy Policy-SSH then count set security policies from-zone untrust to-zone trust policy Policy-HTTP match source-address any set security policies from-zone untrust to-zone trust policy Policy-HTTP match destination-address 10.2.1.2/32 set security policies from-zone untrust to-zone trust policy Policy-HTTP match application junos-http set security policies from-zone untrust to-zone trust policy Policy-HTTP then permit set security zones security-zone trust address-book address 10.2.1.2/32 10.2.1.2/32 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust interfaces vlan.0 set security zones security-zone untrust address-book address 11.11.11.11/32 11.11.11.11/32 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust interfaces pp0.0 set firewall family inet filter Filter1 term Term-ICMP from protocol icmp set firewall family inet filter Filter1 term Term-ICMP then accept set firewall family inet filter Filter1 term Term-MNG from source-address 10.2.1.0/24 set firewall family inet filter Filter1 term Term-MNG from source-address 11.11.11.11/32 set firewall family inet filter Filter1 term Term-MNG from protocol tcp set firewall family inet filter Filter1 term Term-MNG from destination-port ssh set firewall family inet filter Filter1 term Term-MNG from destination-port https set firewall family inet filter Filter1 term Term-MNG then log set firewall family inet filter Filter1 term Term-MNG then accept set vlans default l3-interface vlan.0 root@FW-2>
