Cisco
IPsec IKEv2のデバッグログ
構成図
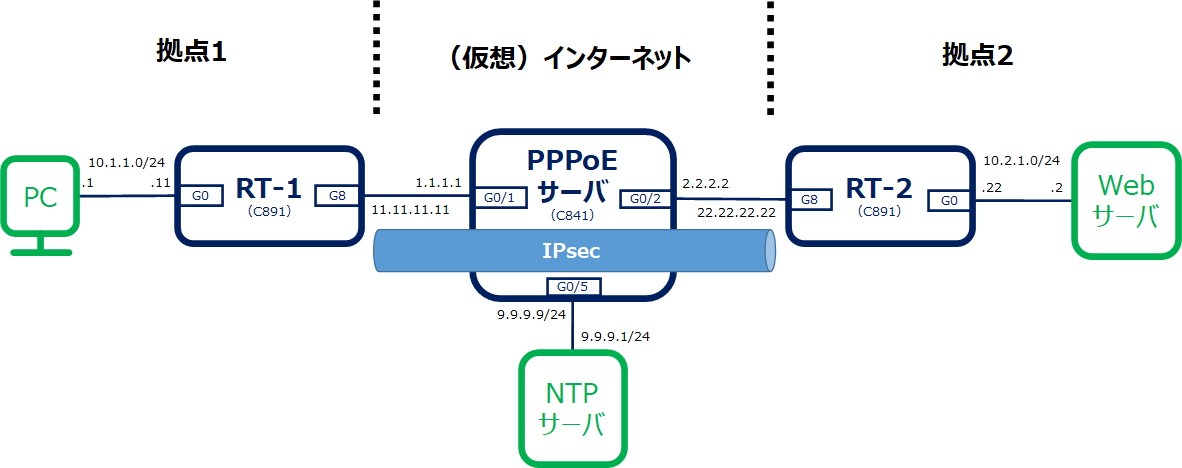
IPsec IKEv2のコンフィグで、IPsecが接続される際のデバッグログを記録します。
RT-1のデバッグログ(イニシエーターとして動作)
RT-1#debug crypto ikev2
IKEv2 default debugging is on
RT-1#
RT-1#debug crypto ipsec
Crypto IPSEC debugging is on
RT-1#
000326: *Nov 16 20:51:08.683: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 11.11.11.11:500, remote= 22.22.22.22:500,
local_proxy= 10.1.1.0/255.255.255.0/256/0,
remote_proxy= 10.2.1.0/255.255.255.0/256/0,
protocol= ESP, transform= esp-aes esp-sha256-hmac (Tunnel),
lifedur= 1200s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
000327: *Nov 16 20:51:08.683: IKEv2:Searching Policy with fvrf 0, local address 11.11.11.11
000328: *Nov 16 20:51:08.683: IKEv2:Found Policy 'Policy-name'
000329: *Nov 16 20:51:08.683: IKEv2:(SESSION ID = 3,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH public key, DH Group 2
000330: *Nov 16 20:51:08.683: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
000331: *Nov 16 20:51:08.683: IKEv2:(SESSION ID = 3,SA ID = 1):Request queued for computation of DH key
000332: *Nov 16 20:51:08.683: IKEv2:IKEv2 initiator - no config data to send in IKE_SA_INIT exch
000333: *Nov 16 20:51:08.683: IKEv2:(SESSION ID = 3,SA ID = 1):Generating IKE_SA_INIT message
000334: *Nov 16 20:51:08.683: IKEv2:(SESSION ID = 3,SA ID = 1):IKE Proposal: 1, SPI size: 0 (initial negotiation),
Num. transforms: 4
AES-CBC SHA256 SHA256 DH_GROUP_1024_MODP/Group 2
000335: *Nov 16 20:51:08.683: IKEv2:(SESSION ID = 3,SA ID = 1):Sending Packet [To 22.22.22.22:500/From 11.11.11.11:500/VRF i0:f0]
Initiator SPI : 3F4707F23174F959 - Responder SPI : 0000000000000000 Message id: 0
IKEv2 IKE_SA_INIT Exchange REQUEST
Payload contents:
SA KE N VID VID NOTIFY(NAT_DETECTION_SOURCE_IP) NOTIFY(NAT_DETECTION_DESTINATION_IP)
000336: *Nov 16 20:51:08.683: IKEv2:(SESSION ID = 3,SA ID = 1):Insert SA
000337: *Nov 16 20:51:08.691: IKEv2:(SESSION ID = 3,SA ID = 1):Received Packet [From 22.22.22.22:500/To 11.11.11.11:500/VRF i0:f0]
Initiator SPI : 3F4707F23174F959 - Responder SPI : FB1A112B17F492AE Message id: 0
IKEv2 IKE_SA_INIT Exchange RESPONSE
Payload contents:
SA KE N VID VID NOTIFY(NAT_DETECTION_SOURCE_IP) NOTIFY(NAT_DETECTION_DESTINATION_IP)
000338: *Nov 16 20:51:08.691: IKEv2:(SESSION ID = 3,SA ID = 1):Processing IKE_SA_INIT message
000339: *Nov 16 20:51:08.691: IKEv2:(SESSION ID = 3,SA ID = 1):Verify SA init message
000340: *Nov 16 20:51:08.691: IKEv2:(SESSION ID = 3,SA ID = 1):Processing IKE_SA_INIT message
000341: *Nov 16 20:51:08.691: IKEv2:(SESSION ID = 3,SA ID = 1):Checking NAT discovery
000342: *Nov 16 20:51:08.691: IKEv2:(SESSION ID = 3,SA ID = 1):NAT not found
000343: *Nov 16 20:51:08.691: IKEv2:(SESSION ID = 3,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH secret key, DH Group 2
000344: *Nov 16 20:51:08.691: IKEv2:(SESSION ID = 3,SA ID = 1):Request queued for computation of DH secret
000345: *Nov 16 20:51:08.695: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
000346: *Nov 16 20:51:08.695: IKEv2:(SA ID = 1):[IKEv2 -> Crypto Engine] Calculate SKEYSEED and create rekeyed IKEv2 SA
000347: *Nov 16 20:51:08.695: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] SKEYSEED calculation and creation of rekeyed IKEv2 SA PASSED
000348: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Completed SA init exchange
000349: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Check for EAP exchange
000350: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Generate my authentication data
000351: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Use preshared key for id 11.11.11.11, key len 6
000352: *Nov 16 20:51:08.695: IKEv2:[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data
000353: *Nov 16 20:51:08.695: IKEv2:[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED
000354: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Get my authentication method
000355: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):My authentication method is 'PSK'
000356: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Check for EAP exchange
000357: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Generating IKE_AUTH message
000358: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Constructing IDi payload: '11.11.11.11' of type 'IPv4 address'
000359: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):ESP Proposal: 1, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
AES-CBC SHA256 Don't use ESN
000360: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Building packet for encryption.
Payload contents:
VID IDi AUTH SA TSi TSr NOTIFY(INITIAL_CONTACT) NOTIFY(SET_WINDOW_SIZE) NOTIFY(ESP_TFC_NO_SUPPORT) NOTIFY(NON_FIRST_FRAGS)
000361: *Nov 16 20:51:08.695: IKEv2:(SESSION ID = 3,SA ID = 1):Sending Packet [To 22.22.22.22:500/From 11.11.11.11:500/VRF i0:f0]
Initiator SPI : 3F4707F23174F959 - Responder SPI : FB1A112B17F492AE Message id: 1
IKEv2 IKE_AUTH Exchange REQUEST
Payload contents:
ENCR
000362: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Received Packet [From 22.22.22.22:500/To 11.11.11.11:500/VRF i0:f0]
Initiator SPI : 3F4707F23174F959 - Responder SPI : FB1A112B17F492AE Message id: 1
IKEv2 IKE_AUTH Exchange RESPONSE
Payload contents:
VID IDr AUTH SA TSi TSr NOTIFY(SET_WINDOW_SIZE) NOTIFY(ESP_TFC_NO_SUPPORT) NOTIFY(NON_FIRST_FRAGS)
000363: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Process auth response notify
000364: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Searching policy based on peer's identity '22.22.22.22' of type 'IPv4 address'
000365: *Nov 16 20:51:08.703: IKEv2:Searching Policy with fvrf 0, local address 11.11.11.11
000366: *Nov 16 20:51:08.703: IKEv2:Found Policy 'Policy-name'
000367: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Verify peer's policy
000368: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Peer's policy verified
000369: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Get peer's authentication method
000370: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Peer's authentication method is 'PSK'
000371: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Get peer's preshared key for 22.22.22.22
000372: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Verify peer's authentication data
000373: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Use preshared key for id 22.22.22.22, key len 6
000374: *Nov 16 20:51:08.703: IKEv2:[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data
000375: *Nov 16 20:51:08.703: IKEv2:[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED
000376: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Verification of peer's authenctication data PASSED
000377: *Nov 16 20:51:08.703: IKEv2:(SESSION ID = 3,SA ID = 1):Check for EAP exchange
000378: *Nov 16 20:51:08.707: IKEv2:(SESSION ID = 3,SA ID = 1):Processing IKE_AUTH message
000379: *Nov 16 20:51:08.707: IKEv2:KMI/verify policy/sending to IPSec:
prot: 3 txfm: 12 hmac 5 flags 16369 keysize 128 IDB 0x12151A54
000380: *Nov 16 20:51:08.707: IPSEC(validate_proposal_request): proposal part #1
000381: *Nov 16 20:51:08.707: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 10.1.1.0/255.255.255.0/256/0,
remote_proxy= 10.2.1.0/255.255.255.0/256/0,
protocol= ESP, transform= NONE (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
000382: *Nov 16 20:51:08.707: Crypto mapdb : proxy_match
src addr : 10.1.1.0
dst addr : 10.2.1.0
protocol : 0
src port : 0
dst port : 0
000383: *Nov 16 20:51:08.707: (ipsec_process_proposal)Map Accepted: MAP-name, 160
000384: *Nov 16 20:51:08.707: IKEv2:(SESSION ID = 3,SA ID = 1):IKEV2 SA created; inserting SA into database. SA lifetime timer (1800 sec) started
000385: *Nov 16 20:51:08.707: IKEv2:(SESSION ID = 3,SA ID = 1):Session with IKE ID PAIR (22.22.22.22, 11.11.11.11) is UP
000386: *Nov 16 20:51:08.707: IKEv2:(SESSION ID = 3,SA ID = 1):Initializing DPD, configured for 30 seconds
000387: *Nov 16 20:51:08.707: IKEv2:IKEv2 MIB tunnel started, tunnel index 1
000388: *Nov 16 20:51:08.707: IKEv2:(SESSION ID = 3,SA ID = 1):Load IPSEC key material
000389: *Nov 16 20:51:08.707: IKEv2:(SA ID = 1):[IKEv2 -> IPsec] Create IPsec SA into IPsec database
000390: *Nov 16 20:51:08.707: IPSEC(key_engine): got a queue event with 1 KMI message(s)
000391: *Nov 16 20:51:08.707: Crypto mapdb : proxy_match
src addr : 10.1.1.0
dst addr : 10.2.1.0
protocol : 256
src port : 0
dst port : 0
000392: *Nov 16 20:51:08.707: IPSEC:(SESSION ID = 3) (crypto_ipsec_create_ipsec_sas) Map found MAP-name, 160
000393: *Nov 16 20:51:08.707: IPSEC:(SESSION ID = 3) (crypto_ipsec_sa_find_ident_head) reconnecting with the same proxies and peer 22.22.22.22
000394: *Nov 16 20:51:08.707: IPSEC:(SESSION ID = 3) (create_sa) sa created,
(sa) sa_dest= 11.11.11.11, sa_proto= 50,
sa_spi= 0x6753C32D(1733542701),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 24
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 10.1.1.0/255.255.255.0/256/0,
remote_proxy= 10.2.1.0/255.255.255.0/256/0
000395: *Nov 16 20:51:08.707: IPSEC:(SESSION ID = 3) (create_sa) sa created,
(sa) sa_dest= 22.22.22.22, sa_proto= 50,
sa_spi= 0xF2298290(4062806672),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 23
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 11.11.11.11:0, remote= 22.22.22.22:0,
local_proxy= 10.1.1.0/255.255.255.0/256/0,
remote_proxy= 10.2.1.0/255.255.255.0/256/0
000396: *Nov 16 20:51:08.707: IPSEC: Expand action denied, notify RP
000397: *Nov 16 20:51:08.707: IKEv2:(SA ID = 1):[IPsec -> IKEv2] Creation of IPsec SA into IPsec database PASSED
000398: *Nov 16 20:51:08.707: IKEv2:(SESSION ID = 3,SA ID = 1):Checking for duplicate IKEv2 SA
RT-1#
000399: *Nov 16 20:51:08.707: IKEv2:(SESSION ID = 3,SA ID = 1):No duplicate IKEv2 SA found
RT-1#no debug all
All possible debugging has been turned off
RT-2のデバッグログ(レスポンダーとして動作)
RT-2#debug crypto ikev2
IKEv2 default debugging is on
RT-2#
RT-2#debug crypto ipsec
Crypto IPSEC debugging is on
RT-2#
000318: *Nov 16 19:32:53.187: IKEv2:Received Packet [From 11.11.11.11:500/To 22.22.22.22:500/VRF i0:f0]
Initiator SPI : 3F4707F23174F959 - Responder SPI : 0000000000000000 Message id: 0
IKEv2 IKE_SA_INIT Exchange REQUEST
Payload contents:
SA KE N VID VID NOTIFY(NAT_DETECTION_SOURCE_IP) NOTIFY(NAT_DETECTION_DESTINATION_IP)
000319: *Nov 16 19:32:53.187: IKEv2:(SESSION ID = 9,SA ID = 1):Verify SA init message
000320: *Nov 16 19:32:53.187: IKEv2:(SESSION ID = 9,SA ID = 1):Insert SA
000321: *Nov 16 19:32:53.191: IKEv2:Searching Policy with fvrf 0, local address 22.22.22.22
000322: *Nov 16 19:32:53.191: IKEv2:Found Policy 'Policy-name'
000323: *Nov 16 19:32:53.191: IKEv2:(SESSION ID = 9,SA ID = 1):Processing IKE_SA_INIT message
000324: *Nov 16 19:32:53.191: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Retrieve configured trustpoint(s)
000325: *Nov 16 19:32:53.191: IKEv2:(SA ID = 1):[PKI -> IKEv2] Retrieved trustpoint(s): NONE
000326: *Nov 16 19:32:53.191: IKEv2:Failed to retrieve Certificate Issuer list
000327: *Nov 16 19:32:53.191: IKEv2:(SESSION ID = 9,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH public key, DH Group 2
000328: *Nov 16 19:32:53.191: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
000329: *Nov 16 19:32:53.191: IKEv2:(SESSION ID = 9,SA ID = 1):Request queued for computation of DH key
000330: *Nov 16 19:32:53.191: IKEv2:(SESSION ID = 9,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH secret key, DH Group 2
000331: *Nov 16 19:32:53.191: IKEv2:(SESSION ID = 9,SA ID = 1):Request queued for computation of DH secret
000332: *Nov 16 19:32:53.191: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
000333: *Nov 16 19:32:53.191: IKEv2:(SA ID = 1):[IKEv2 -> Crypto Engine] Calculate SKEYSEED and create rekeyed IKEv2 SA
000334: *Nov 16 19:32:53.191: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] SKEYSEED calculation and creation of rekeyed IKEv2 SA PASSED
000335: *Nov 16 19:32:53.191: IKEv2:IKEv2 responder - no config data to send in IKE_SA_INIT exch
000336: *Nov 16 19:32:53.191: IKEv2:(SESSION ID = 9,SA ID = 1):Generating IKE_SA_INIT message
000337: *Nov 16 19:32:53.191: IKEv2:(SESSION ID = 9,SA ID = 1):IKE Proposal: 1, SPI size: 0 (initial negotiation),
Num. transforms: 4
AES-CBC SHA256 SHA256 DH_GROUP_1024_MODP/Group 2
000338: *Nov 16 19:32:53.191: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Retrieve configured trustpoint(s)
000339: *Nov 16 19:32:53.191: IKEv2:(SA ID = 1):[PKI -> IKEv2] Retrieved trustpoint(s): NONE
000340: *Nov 16 19:32:53.191: IKEv2:Failed to retrieve Certificate Issuer list
000341: *Nov 16 19:32:53.195: IKEv2:(SESSION ID = 9,SA ID = 1):Sending Packet [To 11.11.11.11:500/From 22.22.22.22:500/VRF i0:f0]
Initiator SPI : 3F4707F23174F959 - Responder SPI : FB1A112B17F492AE Message id: 0
IKEv2 IKE_SA_INIT Exchange RESPONSE
Payload contents:
SA KE N VID VID NOTIFY(NAT_DETECTION_SOURCE_IP) NOTIFY(NAT_DETECTION_DESTINATION_IP)
000342: *Nov 16 19:32:53.195: IKEv2:(SESSION ID = 9,SA ID = 1):Completed SA init exchange
000343: *Nov 16 19:32:53.195: IKEv2:(SESSION ID = 9,SA ID = 1):Starting timer (30 sec) to wait for auth message
000344: *Nov 16 19:32:53.199: IKEv2:(SESSION ID = 9,SA ID = 1):Received Packet [From 11.11.11.11:500/To 22.22.22.22:500/VRF i0:f0]
Initiator SPI : 3F4707F23174F959 - Responder SPI : FB1A112B17F492AE Message id: 1
IKEv2 IKE_AUTH Exchange REQUEST
Payload contents:
VID IDi AUTH SA TSi TSr NOTIFY(INITIAL_CONTACT) NOTIFY(SET_WINDOW_SIZE) NOTIFY(ESP_TFC_NO_SUPPORT) NOTIFY(NON_FIRST_FRAGS)
000345: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Stopping timer to wait for auth message
000346: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Checking NAT discovery
000347: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):NAT not found
000348: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Searching policy based on peer's identity '11.11.11.11' of type 'IPv4 address'
000349: *Nov 16 19:32:53.203: IKEv2:found matching IKEv2 profile 'Profile-name'
000350: *Nov 16 19:32:53.203: IKEv2:Searching Policy with fvrf 0, local address 22.22.22.22
000351: *Nov 16 19:32:53.203: IKEv2:Found Policy 'Policy-name'
000352: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Verify peer's policy
000353: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Peer's policy verified
000354: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Get peer's authentication method
000355: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Peer's authentication method is 'PSK'
000356: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Get peer's preshared key for 11.11.11.11
000357: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Verify peer's authentication data
000358: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Use preshared key for id 11.11.11.11, key len 6
000359: *Nov 16 19:32:53.203: IKEv2:[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data
000360: *Nov 16 19:32:53.203: IKEv2:[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED
000361: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Verification of peer's authenctication data PASSED
000362: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Processing INITIAL_CONTACT
000363: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Processing IKE_AUTH message
000364: *Nov 16 19:32:53.203: IKEv2:KMI/verify policy/sending to IPSec:
prot: 3 txfm: 12 hmac 5 flags 16369 keysize 128 IDB 0x0
000365: *Nov 16 19:32:53.203: IPSEC(validate_proposal_request): proposal part #1
000366: *Nov 16 19:32:53.203: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 10.2.1.0/255.255.255.0/256/0,
remote_proxy= 10.1.1.0/255.255.255.0/256/0,
protocol= ESP, transform= NONE (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
000367: *Nov 16 19:32:53.203: Crypto mapdb : proxy_match
src addr : 10.2.1.0
dst addr : 10.1.1.0
protocol : 0
src port : 0
dst port : 0
000368: *Nov 16 19:32:53.203: (ipsec_process_proposal)Map Accepted: MAP-name, 160
000369: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Get my authentication method
000370: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):My authentication method is 'PSK'
000371: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Get peer's preshared key for 11.11.11.11
000372: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Generate my authentication data
000373: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Use preshared key for id 22.22.22.22, key len 6
000374: *Nov 16 19:32:53.203: IKEv2:[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data
000375: *Nov 16 19:32:53.203: IKEv2:[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED
000376: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Get my authentication method
000377: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):My authentication method is 'PSK'
000378: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Generating IKE_AUTH message
000379: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Constructing IDr payload: '22.22.22.22' of type 'IPv4 address'
000380: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):ESP Proposal: 1, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
AES-CBC SHA256 Don't use ESN
000381: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Building packet for encryption.
Payload contents:
VID IDr AUTH SA TSi TSr NOTIFY(SET_WINDOW_SIZE) NOTIFY(ESP_TFC_NO_SUPPORT) NOTIFY(NON_FIRST_FRAGS)
000382: *Nov 16 19:32:53.203: IKEv2:(SESSION ID = 9,SA ID = 1):Sending Packet [To 11.11.11.11:500/From 22.22.22.22:500/VRF i0:f0]
Initiator SPI : 3F4707F23174F959 - Responder SPI : FB1A112B17F492AE Message id: 1
IKEv2 IKE_AUTH Exchange RESPONSE
Payload contents:
ENCR
000383: *Nov 16 19:32:53.207: IKEv2:(SESSION ID = 9,SA ID = 1):IKEV2 SA created; inserting SA into database. SA lifetime timer (1800 sec) started
000384: *Nov 16 19:32:53.207: IKEv2:(SESSION ID = 9,SA ID = 1):Session with IKE ID PAIR (11.11.11.11, 22.22.22.22) is UP
000385: *Nov 16 19:32:53.207: IKEv2:(SESSION ID = 9,SA ID = 1):Initializing DPD, configured for 30 seconds
000386: *Nov 16 19:32:53.207: IKEv2:IKEv2 MIB tunnel started, tunnel index 1
000387: *Nov 16 19:32:53.207: IKEv2:(SESSION ID = 9,SA ID = 1):Load IPSEC key material
000388: *Nov 16 19:32:53.207: IKEv2:(SA ID = 1):[IKEv2 -> IPsec] Create IPsec SA into IPsec database
000389: *Nov 16 19:32:53.207: IPSEC(key_engine): got a queue event with 1 KMI message(s)
000390: *Nov 16 19:32:53.207: Crypto mapdb : proxy_match
src addr : 10.2.1.0
dst addr : 10.1.1.0
protocol : 256
src port : 0
dst port : 0
000391: *Nov 16 19:32:53.207: IPSEC:(SESSION ID = 9) (crypto_ipsec_create_ipsec_sas) Map found MAP-name, 160
000392: *Nov 16 19:32:53.207: IPSEC:(SESSION ID = 9) (create_sa) sa created,
(sa) sa_dest= 22.22.22.22, sa_proto= 50,
sa_spi= 0xF2298290(4062806672),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 23
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 10.2.1.0/255.255.255.0/256/0,
remote_proxy= 10.1.1.0/255.255.255.0/256/0
000393: *Nov 16 19:32:53.207: IPSEC:(SESSION ID = 9) (create_sa) sa created,
(sa) sa_dest= 11.11.11.11, sa_proto= 50,
sa_spi= 0x6753C32D(1733542701),
sa_trans= esp-aes esp-sha256-hmac , sa_conn_id= 24
sa_lifetime(k/sec)= (4608000/1200),
(identity) local= 22.22.22.22:0, remote= 11.11.11.11:0,
local_proxy= 10.2.1.0/255.255.255.0/256/0,
remote_proxy= 10.1.1.0/255.255.255.0/256/0
000394: *Nov 16 19:32:53.207: IPSEC: Expand action denied, notify RP
000395: *Nov 16 19:32:53.207: IKEv2:(SA ID = 1):[IPsec -> IKEv2] Creation of IPsec SA into IPsec database PASSED
000396: *Nov 16 19:32:53.207: IKEv2:(SESSION ID = 9,SA ID = 1):Checking for duplicate IKEv2 SA
000397: *Nov 16 19:32:53.207: IKEv2:(SESSION ID = 9,SA ID = 1):No duplicate IKEv2 SA found
000398: *Nov 16 19:32:53.207: IKEv2:(SESSION ID = 9,SA ID = 1):Starting timer (8 sec) to delete negotiation context
RT-2#
RT-2#no debug all
All possible debugging has been turned off
